Matrix: 1 walkthrough
Description
Description: Matrix is a medium level boot2root challenge. The OVA has been tested on both VMware and Virtual Box. Download from this link
Difficulty: Intermediate
Flags: Your Goal is to get root and read /root/flag.txt
Networking: DHCP: Enabled IP Address: Automatically assigned
Hint: Follow your intuitions … and enumerate!
Recon
We start off running nmap on the box, the port scan paints a clear picture of the open ports as well as the services running behind the ports. In this case, we have ports 22, 80, and 31337. Port 22 running OpenSSH 7.7, port 80 running SimpleHTTPServer 0.6 and, port 31337 also running SimpleHTTPServer 0.6.

Enumeration on the web service
Since we have an active web service running, we check out all possible clues which may be left out on the front facing side, as well as any directories which may be having further information on the box.

Quite interesting, we already have something under port 31337, let’s keep it at the back of our minds for a quick minute, let’s check out the front end on port80.
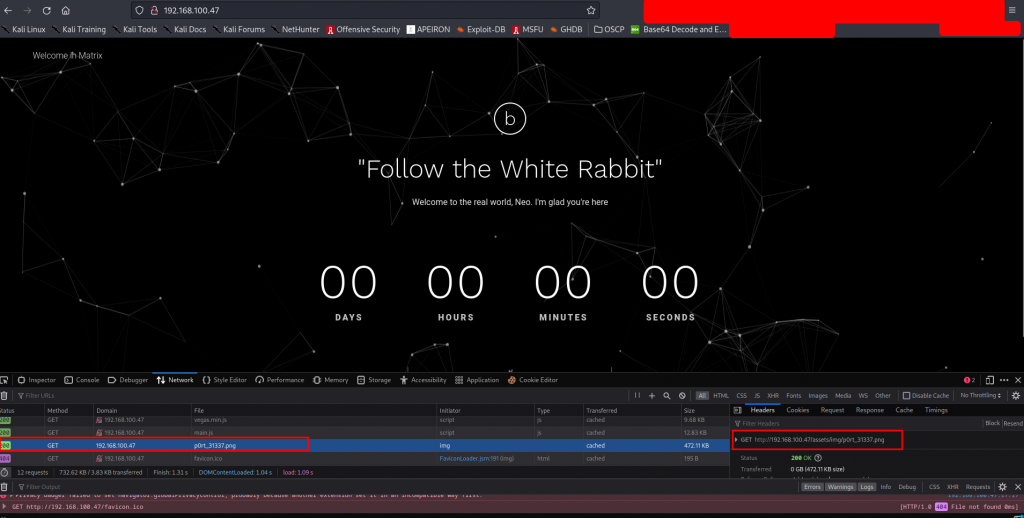
Checking out the directory listings, there’s nothing much going on.
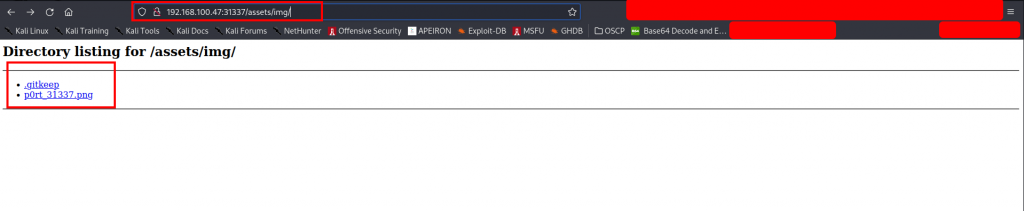
Let’s follow the rabbit……not into the rabbit hole though, stay focused.
Quite interesting…. let’s keep looking.
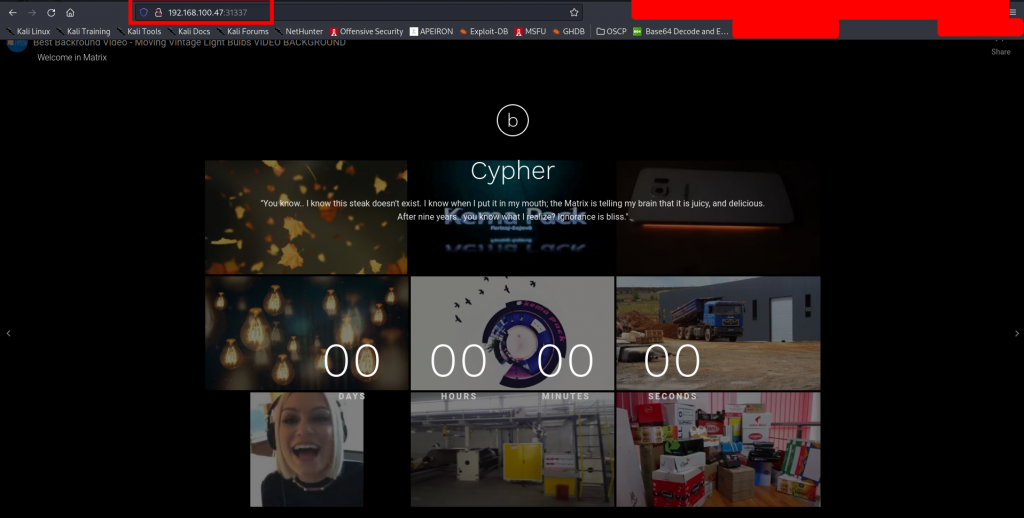
On the source page, we find quite an interesting string lying around, further checks confirm that it’s a base64 encoded string.
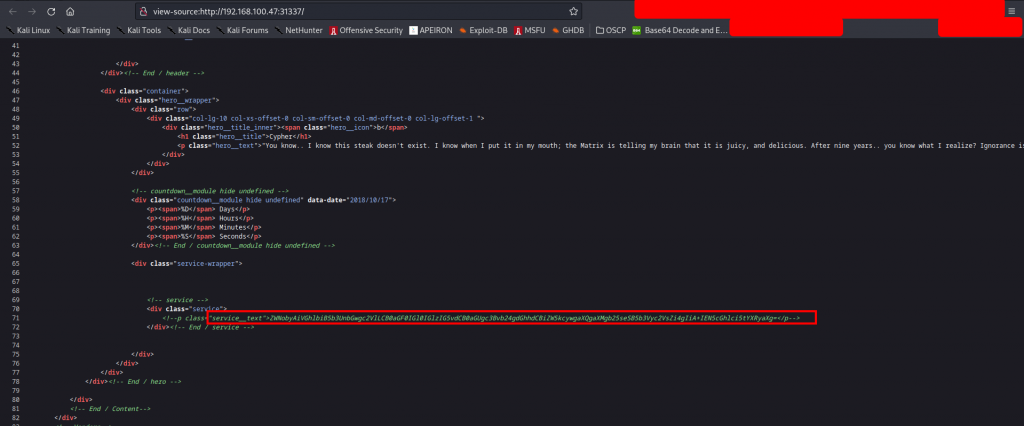
After decoding the base64 string, we find the message:
echo “Then you’ll see, that it is not the spoon that bends, it is only yourself. ” > Cypher.matrix
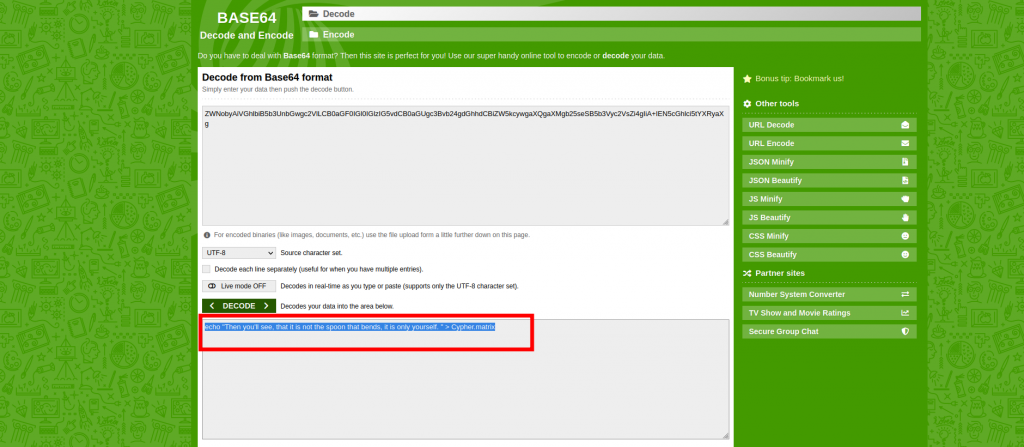
Since we already have a clue, let’s run it on port 31337 or rather http://192.168.100.47:31337/Cypher.matrix.
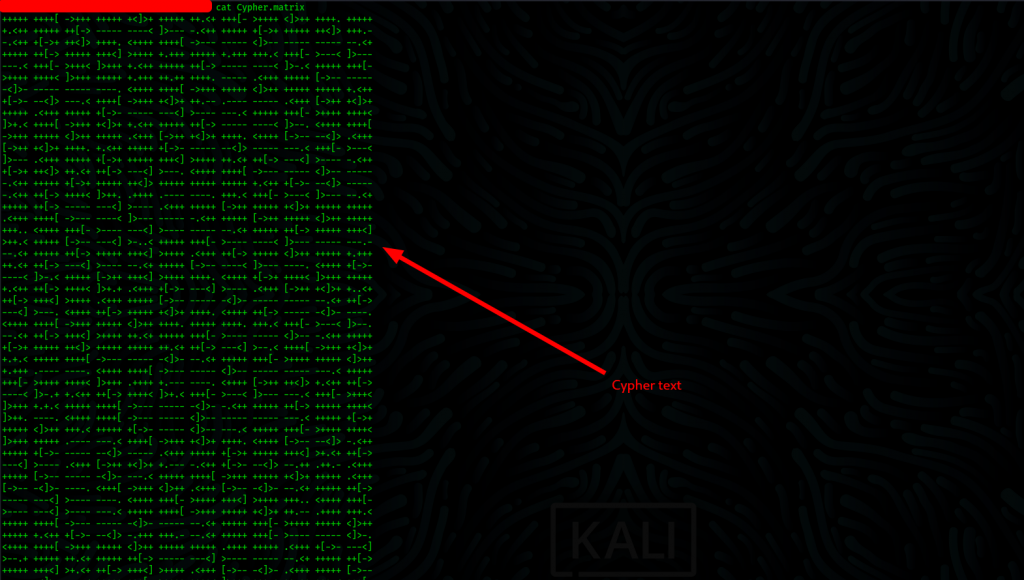
This gives us a download for the file Cypher.matrix which honestly is a mind bender. Since we can’t get the most out of it, we head out to https://copy.sh/brainfuck/ to extract an understandable output.
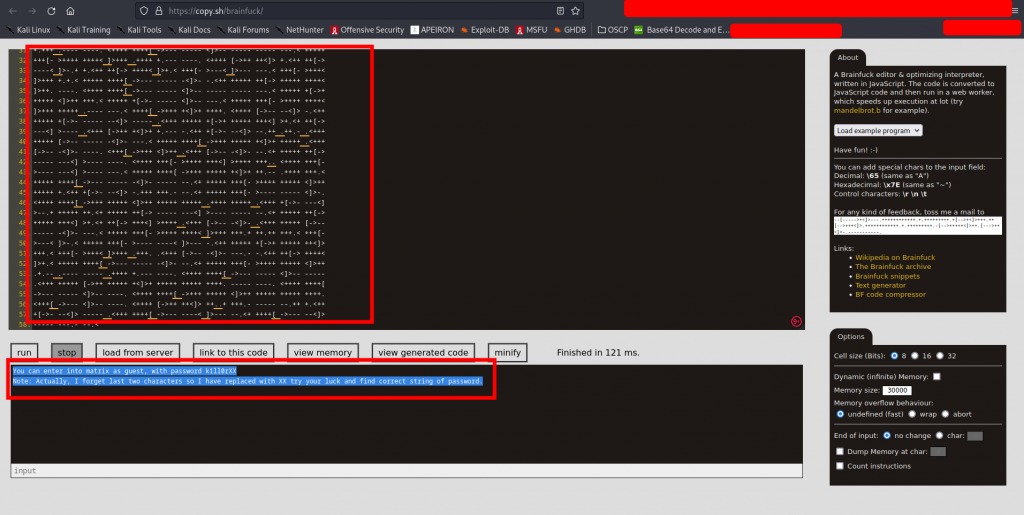
The output:
You can enter into matrix as guest, with password k1ll0rXX
Note: Actually, I forget last two characters so I have replaced with XX try your luck and find correct string of password.
There, we have the credentials, not in full though. We must get the combination of the last two characters of the password. For this scenario, we use the tool mp64 which is a character
generator that can output possible characters, to fill in the last 2 characters for our incomplete password.

After using mp64 to generate the possible combinations of the last missing two characters, we can use hydra to brute force ssh.
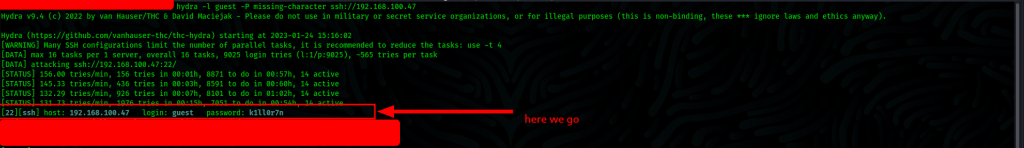
Initial foothold
We’re in
username: guest
Password: k1ll0r7n

We notice our initial foothold is met by rbash which is a Linux Shell that restrict some of the features of bash shell.

In order to log in with proper shell, we can escape the rbash by logging in with the syntax: -→ ssh
guest@192.168.100.47 -t “bash –noprofile” and voilà we’re in.
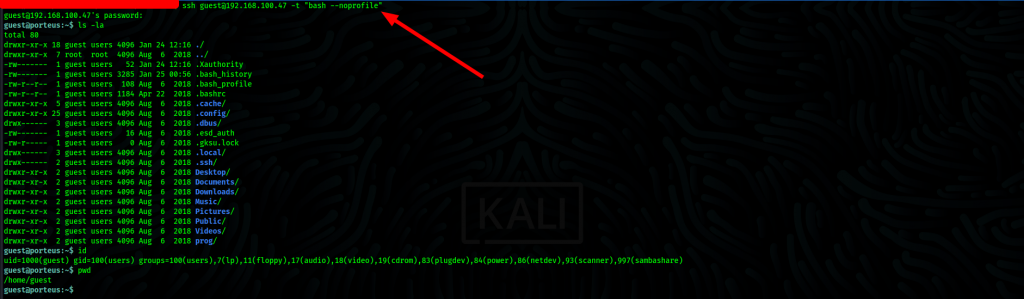
privilege escalation
Initial tinkering around in an attempt to escalate privileges to root, the first attempt is to run the sudo -l command, which gives us an interesting output.

So all we need is to gain root access is run sudo su and we are root.
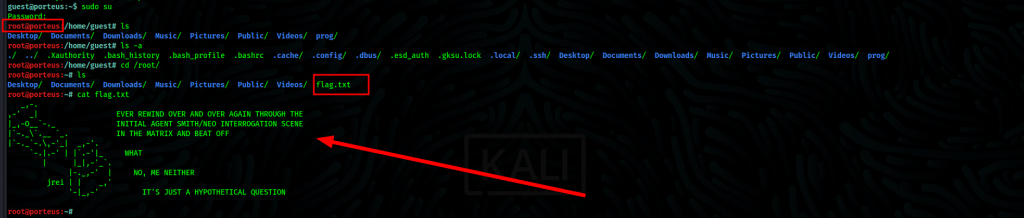
That’s it, we are root, till the next one, step outside the matrix.